Securely enabling our future—a conversation on upcoming attack vectors
With our dependence on IoT devices expected to skyrocket, it's critical to consider plausible scenarios of attacks based upon our understanding of how these devices will serve our needs in the future.
 Image from page 351 of "The principles of mechanics." (source: Internet Archive on Flickr)
Image from page 351 of "The principles of mechanics." (source: Internet Archive on Flickr)
We’ve seen a whole range of new attack vectors and threat agents come into the technology landscape since the dawn of the Internet. Many of the threats have evolved in a fairly predictable way. But because the world around us has come to rely upon interconnected devices at an ever-increasing rate, it’s important for us to ponder the threats to our future.
So far, we have taken a look at vulnerabilities and security principles pertaining to specific devices. We’ve learned a lot about the state of security in IoT devices already in the consumer market. We know the things we are doing wrong today that we need to improve upon to securely enable the devices of the future.
Based on our knowledge of the evolving threat landscape as well as vulnerabilities that have plagued and continue to plague our computing systems and IoT devices, we stand on good ground to be able to predict scenarios that may come to pass. As the use cases served by IoT products evolve, new attack vectors will emerge. In this chapter, we will predict some plausible scenarios of attacks based upon our understanding of how IoT devices will serve our needs in the future.
The Thingbots Have Arrived
Botnets consist of groups of workstations and laptops that have been compromised and are controlled by the botnet owner. Most often the devices are infected by malware sent to the victim via email, by using a phishing website, or by software worms that exploit a vulnerability. A single botnet can comprise thousands of devices, giving the botnet owner tremendous power to launch denial of service attacks on other networks by directing traffic from infected machines toward a specified target (thereby overloading it and preventing it from being able to serve legitimate requests). Botnets are also used to steal private information such as credit card numbers and credentials for bank and email accounts.
The term thingbots is being used in the cybersecurity research industry to describe botnets that include infected IoT devices that can also be leveraged to launch attacks and steal private information. In 2014, a research firm discovered that over 750,000 phishing and spam messages had been sent from more than 100,000 household devices, including televisions, WiFi routers, and fridges.
Thingbot owners are likely to leverage the capabilities of IoT devices to steal information they may not have had access to previously, such as capturing private conversations via infected Smart TVs. They can also take advantage of the ability to control locks and lighting in thousands of homes.
As more IoT devices start to come online, attacks spawned by thingbots are only going to increase, and threat agents are going to have increased access to our private information as well as the ability to cause physical disruptions in our lives. This means that addressing the categories of IoT-related vulnerabilities discussed in this book will become even more of an emergency as we look into our future.
The Rise of the Drones
Unmanned aerial vehicles (UAVs), known in the mainstream media as drones are aircraft without human pilots on board. There are various types of drones, ranging from larger, military-grade ones to drones that are used for recreational purposes such as photography.
At the Black Hat conference in Singapore in 2014, researcher Glenn Wilkinson unveiled a proof-of-concept tool called Snoopy: a quadcopter with two attached video cameras that uses an onboard computer, a GPS unit, and a GSM cellular unit to capture wireless network traffic and follow targets in a defined area. In addition to WiFi, the tool also leverages Bluetooth and radio-frequency identification (RFID) network traffic to track devices and their owners.
The Snoopy software works by tracking network probes from devices such as smartphones that are constantly searching for WiFi networks they have previously associated with. The Snoopy drone then offers a WiFi network with the same name as the one being probed. When a smartphone joins this network, Snoopy proxies the network traffic and therefore can be used to capture data being transmitted by the phone. In addition to phones, Snoopy can also capture data from devices such as pacemakers that use WiFi, as well as fitness devices and smart cards.
The software can be installed on multiple drones that can be spread across a city; Snoopy is designed to capture network data and transmit it to a remote server so the owner of the drones can analyze data in one place. For areas where there is spotty cellular coverage, a single drone can be deployed to hover and capture network traffic while another drone can be sent over periodically to collect the captured data and bring it back to the attacker. The drone also contains an accelerometer that can be used to detect if it has been captured by a third party. In that case, Snoopy can be configured to self-destruct by erasing the contents of the hard drive on the computer attached to the drone.
With researchers being able to demonstrate how UAVs can be leveraged to track people by capturing signals from smartphones and potentially life-sustaining devices such as pacemakers, it’s easy to imagine how drones could be leveraged by heavily funded groups such as state governments and sophisticated criminal gangs. As UAVs continue to evolve in the military and the private space, it is quite probable that they will be used by a variety of agents to gain access to devices and networks. In this book, we have seen many different examples of IoT devices that require no authentication or authorization if the attacker has access to the local WiFi network. The many such popular IoT devices already in existence are going to be a juicy target for individuals and well-funded criminal agencies whose aim is to capture data and possibly compromise people’s physical safety.
Cross-Device Attacks
Many people utilize a slew of computing devices on a daily basis—smartphones, personal and employer-issued laptops and workstations, and tablets—to get their professional and private work done. Quite often, data is synced across multiple devices so the users have access to all their information regardless of what device they’re using. For example, users may back up their smartphones onto their personal laptops. Another example is using a service such as iCloud to sync documents, application settings, and contacts across devices. This creates a situation in which an attacker may be able to leverage one device that has been compromised to access information that is stored on another device or synced across devices via the cloud.
Imagine a situation in which a physician stores information about a patient in a document hosted on Dropbox. If the physician’s desktop were to be compromised using a phishing attack, the attacker could modify the contents of the document, perhaps to alter the dosage of a medication. This document would have its updates synced across other devices, such as a tablet that the physician might use while on duty. The tablet might be configured to have full disk encryption and additional security controls deployed by the physician’s employer, but these controls would be ineffective in this situation since the document was compromised on the doctor’s desktop and automatically synced to the same Dropbox account on the tablet. This illustrates how the compromise of a single device in a user’s ecosystem can be leveraged to negatively affect the integrity of data on other devices.
Local backup files from smartphones and tablets that may be stored on workstations and laptops are also a juicy target for attackers. In not available, we analyzed the token called access_token used by the SmartThings iOS app, which is issued by the server upon successful authentication and remains valid for 18,250 days. An attacker who is able to compromise a SmartThings user’s workstation or laptop could potentially steal such a backup file and collect the access_token, which would be likely to work since it is valid for so long.
The number of devices used by a single user will increase the attack surface. Attackers who have access to a single device will be able to steal private information and influence data synced across devices, as well as steal information that can be used to command IoT devices. Users, system administrators, and IoT device and application designers should think through the ecosystem of devices that users are likely to have, along with the possible threat agents, to architect solutions to mitigate these potential attack scenarios.
Hearing Voices
In 2007, Microsoft came under fire for a security hole in the speech-recognition component of its newly released Windows Vista operating system. A malicious website could simply play an audio file commanding the computer to delete files and empty the recycle bin, and the operating system would readily comply. Alternatively, an attacker could email the audio file to victims and lure them into playing it. Microsoft played down the risk, stating that it would be unlikely for all the conditions required for such an attack to succeed to be met. Furthermore, Microsoft stated that users would likely recognize the attack because they would hear the audio instructions play; however, this assumes the users would be in the vicinity of their computers at the time of the attack, which might not be the case if a delay was used before playing the audio file.
Perhaps one reason this issue wasn’t taken very seriously by users was that not many people leverage the speech function in desktop and laptop computers (except for individuals affected by impairments and related difficulties). When Vista was released in 2007, users primarily used the keyboard, mouse, and trackpad as their modes of input. With the growing popularity of intelligent, voice-operated personal assistant services like Siri and Cortana, however, this is changing. Users are starting to enjoy and find value in commanding their smartphones and other devices with their voices.
Jumping on the digital personal assistant bandwagon, Amazon recently released a product called Echo (Figure 1-1) that is primarily voice operated, along with a companion smartphone app to configure it.
The device is a nine-inch-tall speaker and a set of microphones, and has its default wake word set to “Alexa.” Just as with Siri, you can command the Echo to tell you the weather by saying “Alexa, what is the weather like today?” or ask it trivia questions such as “Alexa, how tall was Michael Jackson?”
The Echo can also be configured to turn Philips lightbulbs (discussed in not available) on or off. As with the hue iOS app, the Echo app can access the hue bridge once you press the button on the bridge to prove physical ownership. It is possible to specify a selection of hue lights to control by placing them into a specific group (e.g., Lights, as shown in Figure 1-2).
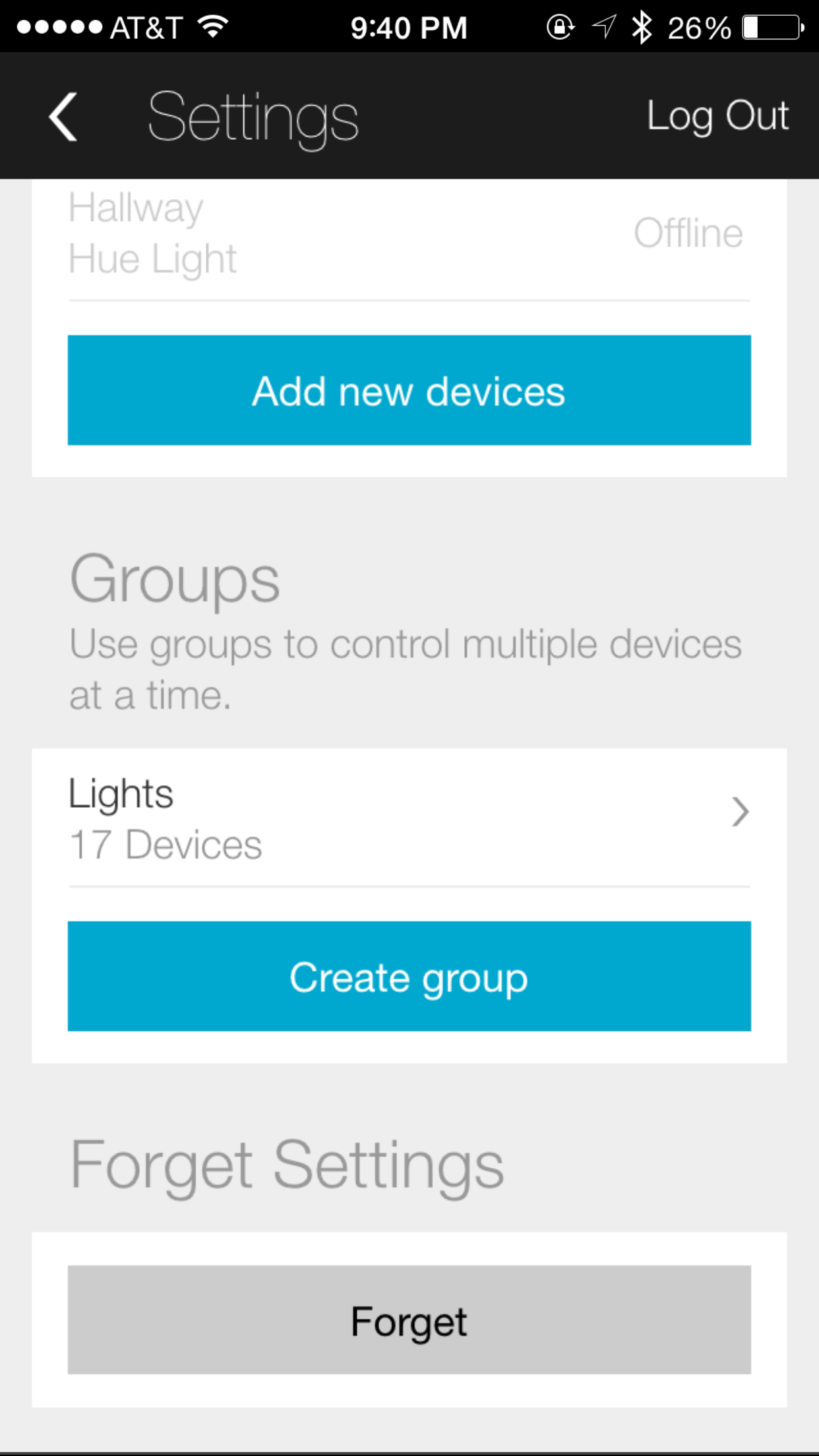
At this point, the user can say “Alexa, turn off lights,” and the Amazon Echo will dutifully cause all 17 lights to go off. Learning from the Microsoft Vista security issue, we can easily simulate a proof-of-concept scenario in which a website plays an audio file instructing Alexa to turn off the lights. Consider a website with the following JavaScript:
<HTML>
<BODY>
<SCRIPT>
var IDLE_TIMEOUT = 60; //in seconds
var _idleSecondsCounter = 0;
document.onclick = function()
{
_idleSecondsCounter = 0;
};
document.onmousemove = function()
{
_idleSecondsCounter = 0;
};
document.onkeypress = function()
{
_idleSecondsCounter = 0;
};
window.setInterval(CheckIdleTime, 1000);
function CheckIdleTime()
{
_idleSecondsCounter++;
if (_idleSecondsCounter >= IDLE_TIMEOUT)
{
var audio = new Audio('alexa_lights_off.m4a');
audio.play();
_idleSecondsCounter = 0;
}
}
</SCRIPT>
</BODY>
</HTML>
This JavaScript (slightly modified from the original version available from http://stackoverflow.com/a/13246534) plays the audio file alexa_lights_off.m4a when the browser notices that there have been no mouse or keyboard movements for 60 seconds. The audio file contains the words, “Alexa, lights off.” This rudimentary proof of concept shows how an external website can use audio assistants like the Amazon Echo to influence connected devices.
Back in 2007, the Windows Vista security issue was not of particular interest to the cybersecurity community since the potential impact and the probability of an attacker being able to pull it off were seen to be low (the voice-activation feature had to be turned on and the microphone needed to be next to the speaker). Today, however, more and more people are relying on audio-based personal assistants such as the Echo. What makes this attack vector of particular concern is that some users will depend upon devices like the Echo to command IoT devices such as lights that could have a physical impact on their safety.
The Amazon Echo also works with IFTTT recipes and can command WeMo Switches (discussed in not available). This makes the Echo a powerful device that is able to control not just lighting in homes, but a range of electronic devices. The Echo only allows the user to select “Alexa” or “Amazon” as the wake word, which must be uttered as the first word in every command so that the Echo knows the user has intended it for the device. Our rudimentary proof of concept would have been thwarted if Amazon required users to select a unique wake word. Of course, threat agents such as neighborhood bullies or malicious entities who were able to eavesdrop on conversations through the cameras in Smart TVs might be able to find out what the unique wake word is set to, but this would substantially limit the risk from threat agents who are unable to access that information.
Designers of products such as the Echo should consider malicious activity that leverages audio as a channel of implementing attack vectors, since these products are primarily designed to communicate using audio. The speech recognition security hole may not have been deemed worthy of concern in the past, but product designers and users need to be extremely cognizant of expanding avenues of abuse using audio channels as we continue to increase our reliance on assistants such as the Echo.
IoT Cloud Infrastructure Attacks
Devices that offer Internet connectivity require supporting cloud infrastructure. We’ve seen how the hue lighting system can be controlled from anywhere in the world using the iOS app. We’ve seen how the WeMo Baby monitor can be accessed remotely through supporting infrastructure hosted by Amazon’s cloud service. We’ve seen how the Tesla Model S maintains a persistent cellular connection with Tesla’s infrastructure to obtain over-the-air updates, send diagnostics, and be controlled using the iOS app. Such reliance of IoT devices upon cloud infrastructure makes it a juicy target for abuse.
In late 2014, hackers compromised the iCloud accounts of several celebrities and exposed their private photographs and videos to the public. They tried various combinations of passwords for the target iCloud accounts until they guessed the right ones. Since most iPhone users elect to sync their photographs and videos across devices using the iCloud service, the attackers were able to obtain the images upon logging in.
Although no actual vulnerability in the iCloud service was discovered to have been exploited, the reason the attackers were easily able to obtain access was that the service did not implement controls to lock out accounts if too many unsuccessful login attempts were made in a given period of time.
This celebrity breach demonstrates how the use of a static password makes it easy for potential attackers to gain access to private information. Sophisticated IoT devices such as the Tesla Model S also use static passwords that can be easily guessed, allowing attackers to track vehicles, unlock them, and even start them and drive away.
In addition to the cloud infrastructure implemented by the IoT device manufacturers themselves, platforms such as IFTTT and Apple’s HomeKit will be included in the potential attack surface. We’ve already seen how easy it is to connect our online spaces, such as email and social networks, with IoT devices such as lightbulbs and door locks. Compromising someone’s IFTTT account gives the attacker control over all of the virtual and physical services tied to the victim’s account.
Apple’s HomeKit service, which is built into iOS, is another example of a platform that will be of interest to attackers. The HomeKit service allows IoT device manufacturers to seamlessly work with Apple devices, even allowing the users to control their devices remotely. The goal of HomeKit is to allow users to easily set up new devices and then control them using Siri. Other big software companies like Google and Microsoft are also implementing frameworks like HomeKit to enable the emergence of consumer-based IoT devices. Frameworks and services such as these will become popular since they allow users to seamlessly interact with and control their IoT devices. Apple has done a good job of setting clear guidelines stating that developers who use HomeKit must not leverage the data gathered from the APIs for advertising and data mining. However, cybersecurity researchers and malicious attackers (including disgruntled employees who have access to these systems) will be drawn to potential vulnerabilities in such services that can be exploited to gain access to data available from various devices in the victims’ homes.
In the recent past, breaches of cloud services have contributed to loss of privacy for victims and financial gain for attackers. In the near future, attackers will look into exploiting cloud services to gain access to and abuse the functionality of IoT devices to further invade our privacy and potentially compromise our physical safety.
Backdoors
There have been various reports that the NSA may have intercepted devices such as network routers and planted backdoors in them. (A backdoor is a software or hardware modification of a device that allows the modifier to monitor and control the device remotely.) American government agencies have also aggressively lobbied for popular hardware and software manufacturers such as Apple, Google, and Microsoft to build in mechanisms that would allow law enforcement agencies to monitor and obtain data from personal devices such as smartphones.
The Chinese government is routinely accused of building backdoors into hardware and software produced in that country. Given that China is a major hub of hardware production, many electronics companies have a major supply chain presence there. The Chinese government has also recently issued new regulations requiring foreign companies to reveal source code and build backdoors into software and hardware sold to Chinese banks.
The amount of power that can be exerted by a threat agent who is able to influence installing a backdoor into an IoT device is clear—and once the knowledge of their existence is made public, competing attackers and threat agents will seek to leverage these backdoors as well.
The Lurking Heartbleed
Heartbleed is a flaw in the OpenSSL library that can be exploited remotely to gain access to memory on a target device, which may include stored data such as cryptographic keys and user credentials. OpenSSL is a popular library that is used by millions of devices to implement the Transport Layer Security (TLS) protocol to securely encrypt electronic communications.
Heartbleed was announced to developers on April 1, 2014, and at the time of disclosure, about 17 percent of Internet-facing web servers (around half a million) were estimated to be vulnerable to attack. Bruce Schneier, a well-known security expert, described Heartbleed as a “catastrophic” issue given how easily it can be exploited by a remote attacker to steal information.
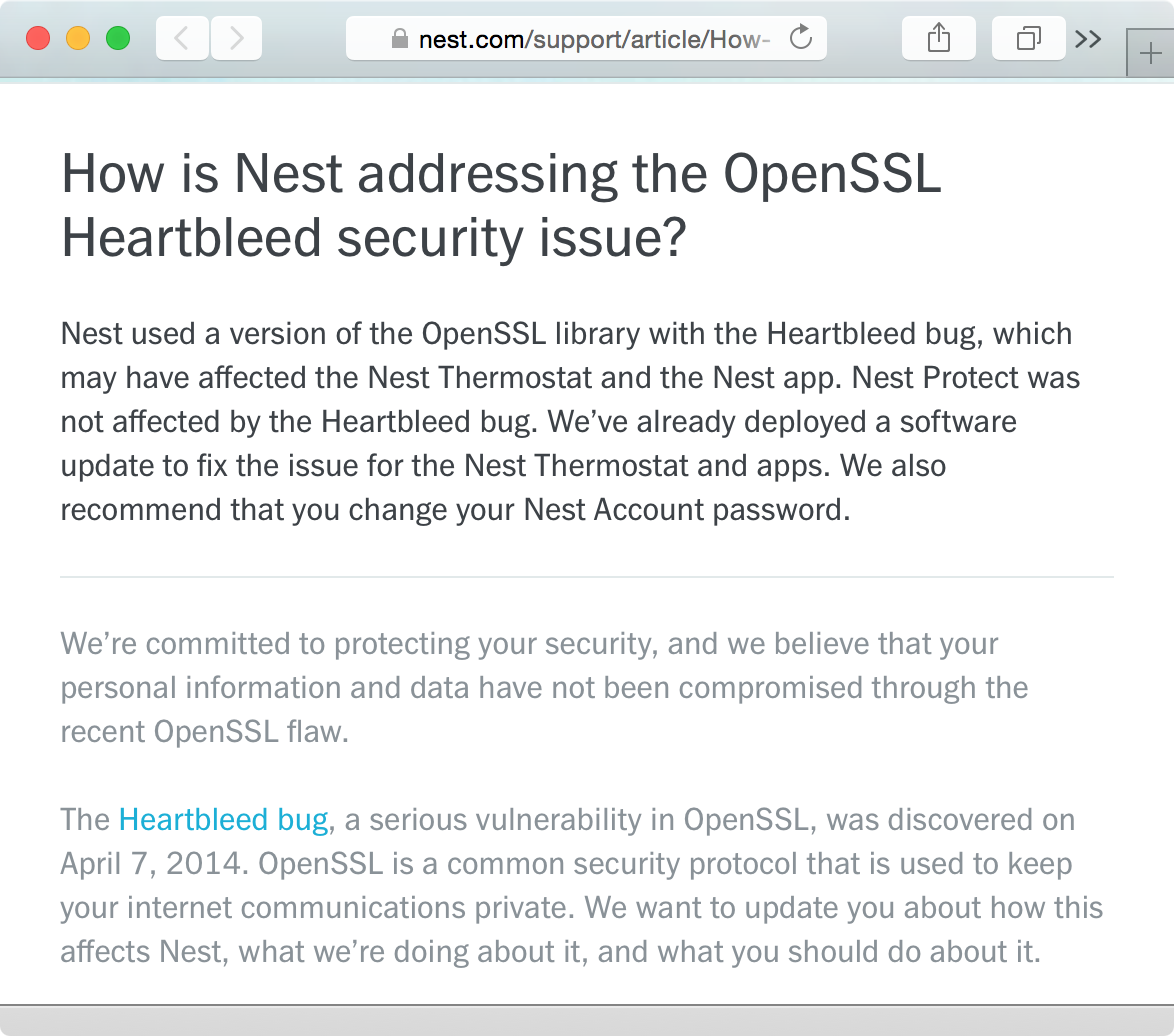
In addition to workstations, IoT devices such as the Nest Thermostat also use OpenSSL. In recognition of this security issue, Nest released an update for its thermostat product and advised its customers to change their Nest passwords in case they had been compromised (Figure 1-3).
Heartbleed demonstrates to us the potentially catastrophic nature of a remotely exploitable vulnerability that can suddenly put millions of IoT devices at risk because they utilize common source code that has a bug in it. Another issue to keep in mind here is that IoT devices without the ability to update firmware and client software will remain vulnerable to critical issues such as this for their lifetime, thereby putting the privacy and safety of their consumers in danger.
Diluting the Medical Record
Vulnerabilities that exploit life-sustaining, hospital-grade devices have been proven. Researcher Jerome Radcliffe has detailed how he was able to use radio communication to remotely instruct an insulin pump to change the dosage being administered. Such an attack could be abused by a malicious entity within wireless range to kill a patient.
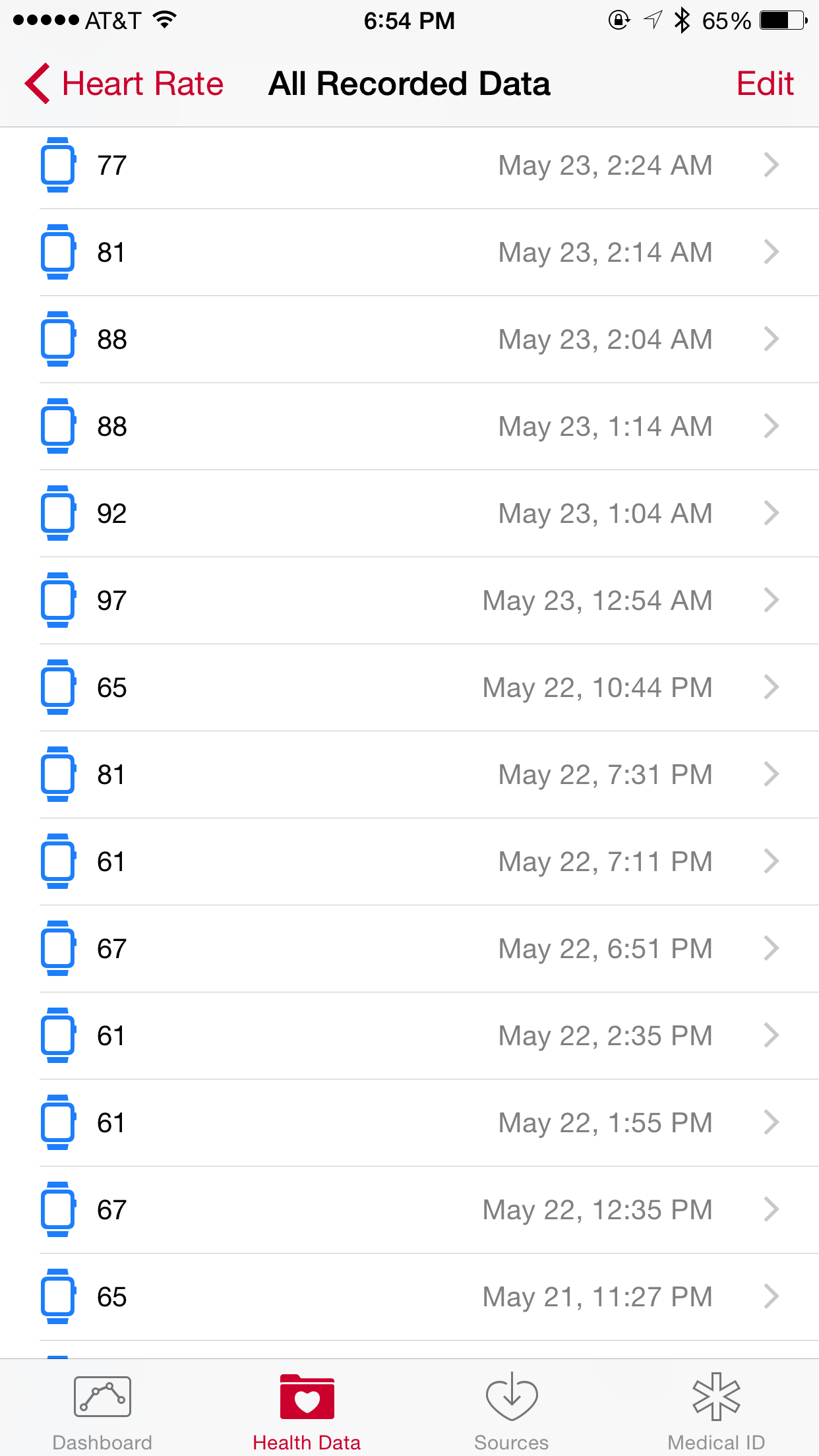
Consumer devices such as Fitbit activity trackers are also gaining attention from the medical community. Doctors find such devices useful to obtain granular information about patients, such as their blood pressure, the amount of daily exercise they get, and other vitals that can influence prescribed dosages and treatments. There is consensus in the medical and technological communities that data from personal activity trackers should be incorporated into patients’ medical records, giving doctors greater visibility into the health of their patients by providing information in addition to what they are able to measure in medical facilities. Figure 1-4 shows a screenshot of heart rate data collected by the Apple Watch using the iOS HealthKit functionality. This information can be extremely useful to medical professionals to help diagnose a patient.
Government regulations and required health approvals will delay the convergence of data collected from personal devices into medical records, yet it is likely that it will eventually happen. Since devices such as the Fitbit and the Apple Watch are able to collect this information, it is valuable to begin to have a conversation on potential abuses of such data. One potential scenario for abuse in this case is the ability of a malicious entity to alter the stored information that is then relied upon by a medical professional. For example, tampering with an <span class=”keep-together”>individual’s</span> heart rate statistics could result in a physician prescribing incorrect dosages of high or low blood pressure medications, which could have significant negative impact on patients’ health.
In addition to monitoring activity, the Health app that comes with the iPhone lets users create an emergency Medical ID (Figure 1-5) that contains vital information such as known medical conditions, medications, blood type, and emergency contacts. This information is available even when the phone is locked so that medical professionals can access it in an emergency.
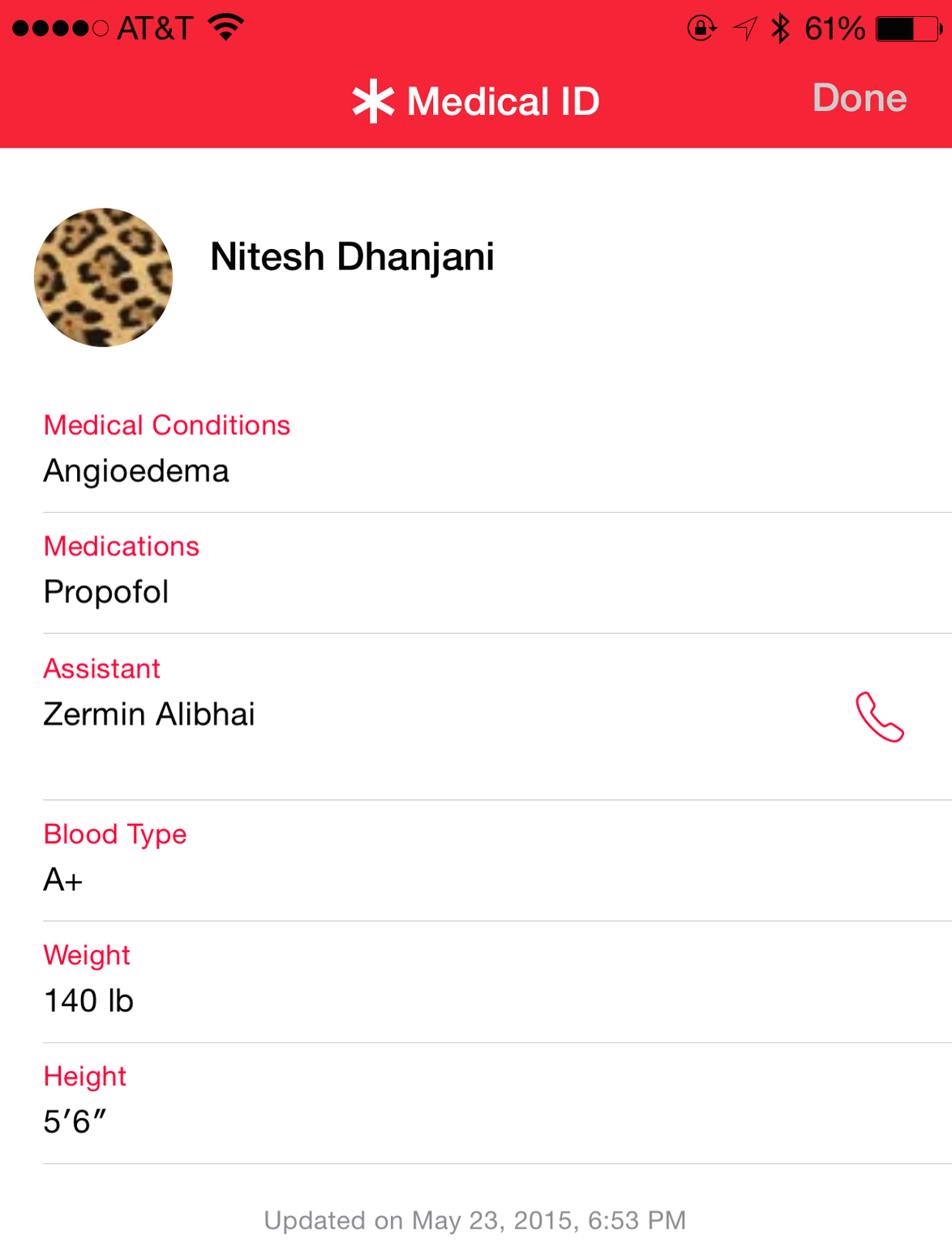
Such a feature undoubtedly has the potential to help save lives by giving doctors vital information in the event of emergencies if the patient is unconscious or unable to communicate. But this information can also put people’s lives at risk, if their iPhones are compromised and the information is purposefully altered. For example, this feature could be abused by acquaintances who have physical access to a person’s iPhone who might want to alter the information in unfortunate cases involving bad family or relationship dynamics or other psychological factors.
Frameworks such as Apple’s ResearchKit are being leveraged by medical researchers to use smartphones and smart watches to collect data and perform research on various diseases and ailments. For example, Stanford Medicine is using ResearchKit to perform a global cardiovascular research study using the MyHeart Counts app. Heartbeat data collected from Apple Watches is sent to a remote database and used to further research. Here is a note from the project’s privacy policy:
All information that is collected through the App will be sent to a secure data server run by Sage BioNetworks (“Sage”), a non-profit research organization. Sage will replace the direct identifiers listed above (your name, email address, and date of birth) with a code to help protect your identity—Sage will encrypt the direct identifiers and store them separately. Because the data are coded, researchers using the data will not be able readily to identify which information pertains to you. Stanford researchers will, however, maintain your consent and personal information and retain the ability to re-identify the information if doing so is needed for research integrity purposes or legal purposes, and they may share re-identified information with others at Stanford who need to see such information to ensure that the research meets legal, regulatory or institutional requirements.
In this case, the information collected is sent to a remote data server. It is then replaced with a random identifier token so researchers using the data will not be able to identify the individual the data is collected from. However, another database is maintained that can be utilized to reidentify the individual should the researchers decide or need to do so. This is a solid example of how health data collected from sensors attached to our bodies is going to be leveraged and possibly distributed across cloud platforms around the world. The security of these platforms, as well as what access the researchers themselves have in terms of identification purposes, will have a bearing on the potential for privacy violations. Medical data stored in the cloud will be open to different attack vectors than traditional medical records stored in hospitals and doctors’ offices.
The Data Tsunami
Most people who use Facebook or Google have noticed targeted ads with a high creep factor—ads on these platforms are tailored to precisely suit people’s interests, based on their previous search queries, email contents, instant messages, and social network dynamics.
Services such as Google now go through your data to suggest events for you to attend, and even offer to check you in for your flights based on an email copy of your itinerary. The world of the IoT will bring in additional sensor- and behavior-based data that will be valuable to social networking companies and extremely useful for marketing. We are likely to see advertisements targeted to us for blood pressure medications based on heart-rate readings from our smart watches, or ads for anti-insomnia drugs based on data collected about what time we usually turn off our IoT-based lighting systems.
As people start to use more IoT devices that they want to integrate and automate using platforms and frameworks provided by companies such as Google and Apple, information collected from various sensors in these devices will become available. This data, which will be used for marketing and stored across multiple cloud architectures, will be a gold mine for malicious agents who have previously been limited to gathering data from online platforms such as email and social networking sites. Besides privacy concerns, the ability of a threat agent to tamper with this information may have health or physical safety implications if the altered information is consumed by other IoT devices. It is likely that such violations of security and privacy will frighten and enrage customers, who will demand the ability to granularly track what data is being collected and how it’s being used, and the ability to opt out.
Targeting Smart Cities
In May 2013, security researchers Billy Rios and Terry McCorkle hacked into the building control system of Google’s Australian headquarters. The building was found to use the Tridium Niagara AX platform, which allows administrators to remotely control physical security alarms, physical access, and heating and air conditioning systems. They were able to obtain access by using the default administrator password of anyonesguess. This password was stored in a configuration file that the researchers obtained by exploiting a vulnerability in the system that exposed this information to unauthenticated users. Tridium systems are popular around the world, and the researchers claimed to have been able to use the Shodan tool to locate more than 25,000 such systems exposed to the Internet.
Besides industrial-grade connected systems like those exploited by Rios and McCorkle, we are starting to see a substantial increase in adoption of consumer-grade IoT devices such as the ones explored in this book thus far. The concept of the smart city (also discussed in not available) combines the use of industrial- and consumer-grade IoT devices to effectively manage energy, healthcare, transport, and waste across a geographical location: smart parking meters and traffic lights in communal spaces coexist with consumer-grade IoT devices installed in homes and directly configurable by citizens (such as lighting, door locks, and cars). Researcher Cesar Cerrudo’s paper “An Emerging US (and World) Threat: Cities Wide Open to Cyber Attacks” covers attack vectors against industrial-grade connected devices that will support the upcoming emergence of the smart city. Currodo’s research and the devices presented in this book will set the stage for attack vectors encompassing smart cities based on various categories of interconnected devices and services.
Efforts by society to construct smart cities are likely to include a curated selection of interconnected devices to provide for consistency and scalability. This brings the drawbacks of monoculture into the discussion. In living species, an advantage of monoculture is low variability in genetics, which in turn results in fewer resources being needed to find medical cures for diseases since experimentation does not require the analysis of a variety of specimens. An associated disadvantage of monoculture is that a new variant of a disease can wipe out the entire population because it will equally affect every individual.
This logic can also be applied to computer systems and IoT devices: increased monoculture will lead to lower costs and ease of interoperability, whereas increased variability will lead to lesser chances of a malicious attack being able to compromise an entire smart city. There are areas of technology, such as the TCP/IP protocol, that are so fundamental to electronic communication that there would be little advantage in attempting to create additional protocols simply to diminish the risks associated with monoculture. However, in areas where there is no one established standard, there can be benefits to variability. The impact of monoculture on systems is an ongoing topic of discussion and debate in the cybersecurity community. It has definite applicability to the concept and emergence of the smart city, and how things develop will ultimately depend upon the total cost of implementation versus the perceived risks that may be introduced.
Interspace Communication Will Be a Ripe Target
One of humankind’s greatest endeavors is our ongoing quest to colonize Mars. NASA plans to send humans to Mars by the 2030s. Its engineers and scientists are working hard to develop the technologies astronauts will use to one day live and work on Mars, and safely return home from the next giant leap for humanity.
Establishing communications between Earth and Mars will be critical in making sure that space agencies are able to successfully transmit crucial data related to the mission and that humans are able to communicate with one another. NASA is aware of the importance of securing communications during space missions:
Reliable communication between ground and spacecraft is central to mission success, especially in the realms of digital communication (data and command links). Seen in the light of recent events, these communication links are vulnerable to malicious intrusion. If terrorists or hackers illegally listen to, or worse, modify communication content, disaster can occur. The consequences of a nuclear powered spacecraft under control of a hacker or terrorist could be devastating. Therefore, all communications to and between spacecraft must be extremely secure and reliable.
There are various projects underway to facilitate interspace communication. For example, NASA’s Optical Communications project is researching ways to use light to transmit data.
Space communication protocols need be robust enough to withstand delays, disruptions, and disconnections in space. Glitches can happen when a spacecraft moves behind a planet, or when solar storms or long communication delays occur. It takes from 4 to 20 minutes to transmit data between Mars and Earth, so NASA’s systems have to tolerate such delays. Therefore, instead of using TCP/IP, NASA has developed a protocol called Disruption-Tolerant Networking (DTN) that is able to work seamlessly during delays and losses of connectivity. DTN is designed to incorporate cryptography and key management, signifying that space agencies are taking steps to make sure security is built into the design of space communication protocols.
NASA isn’t the only player in the area of interspace communication. Elon Musk’s SpaceX is planning on launching a network of low-orbit satellites to provide global Internet access. SpaceX plans to extend this network of satellites to include communications with satellites on Mars when its mission to send humans to Mars comes to fruition.
It is easy to imagine how important communication is going to be to enable critical and risky space missions. Rockets and satellites (and other objects relevant to the mission) are “things” that are going to be available and accessible on space communication infrastructure. As NASA and SpaceX move forward with deploying a greater number of satellites to facilitate networks in space, their architecture will be a ripe target for many threat agents. Terrorists and competing nation-states are likely to attempt to exploit vulnerabilities that may be present in network protocols to steal intellectual property and to disrupt space missions. Such security breaches could result in the loss of human lives or even the failure of humankind to populate other planets. This is going to be an important area for security researchers to contribute to in order to make sure we are building our space communication infrastructure securely from the ground up.
The Dangers of Superintelligence
Irving John Good, a British mathematician who worked as a cryptologist at Bletchley Park with Alan Turing, is often quoted discussing the perils of machines achieving greater intelligence than humans:
Let an ultraintelligent machine be defined as a machine that can far surpass all the intellectual activities of any man however clever. Since the design of machines is one of these intellectual activities, an ultraintelligent machine could design even better machines; there would then unquestionably be an intelligence explosion, and the intelligence of man would be left far behind. Thus the first ultraintelligent machine is the last invention that man need ever make.
Nick Bostrom, author and professor at Oxford, defines superintelligence as “an intellect that is much smarter than the best human brains in practically every field, including scientific creativity, general wisdom and social skills.” Bostrom and other leading scientists are worried that machines capable of superintelligence are going to be difficult to control and that they may have the ability to take over the world and eliminate humankind.
Well-known intellectuals and leaders such as Bill Gates are worried about super intelligence too:
I am in the camp that is concerned about super intelligence. First the machines will do a lot of jobs for us and not be super intelligent. That should be positive if we manage it well. A few decades after that though the intelligence is strong enough to be a concern. I agree with Elon Musk and some others on this and don’t understand why some people are not concerned.
The Future of Life Institute is a volunteer-run research and outreach organization that has been set up to measure and mitigate existential risks facing humanity, including superintelligence. The institute is currently focusing on potential risks from the development of human-level artificial intelligence. Its advisory board includes individuals such as Stephen Hawking, Alan Alda, and Elon Musk, to name a few. This demonstrates that some of the leading minds across various industries are genuinely worried about the perils of superintelligence and that they want to contribute their time and effort to make sure we think through the risks appropriately.
As we get closer to designing machines that are capable of superintelligence, it is likely that professionals with cybersecurity experience are going to be called upon to assist in designing algorithms that can help curtail potentially intelligent machines by running simulations of artificial intelligence in a controlled environment (a sandbox) that protects the safety of human beings.
Computing devices capable of greater levels of intelligence will have access to IoT devices that they can control. The intelligent code itself will be a “thing” on the network it is executed on and may have the intelligence to branch out onto other networks. The unique risk with superintelligence is that large-scale catastrophes may occur if scientists in the lab are not able a superintelligent machine in ways they originally thought they could. It is easy to see how the knowledge of how to create and unleash superintelligent computers could be attractive to terrorists who want to wreak destruction and havoc.
The threat of superintelligence is at the top of the minds of many scientists and researchers in the area of computer science, and this is quite likely the greatest human-made existential threat to humankind.
Conclusion
From thingbots to drones to device backdoors, the attack surface presented by interconnected devices is going to be attractive to threat agents and provide them with unparalleled opportunities to compromise our privacy and physical safety.
Vulnerabilities such as Heartbleed that suddenly affect millions of computing devices have already been known to impact IoT devices, such as the Nest Thermostat. It is quite likely that many other IoT devices in the market are vulnerable to Heartbleed and will continue to be vulnerable due to lack of security patches, either because the vendors have not released them or because the patches were not applied or failed. There are also devices that do not incorporate any mechanism for patches to be applied, and these devices will remain insecure (and potentially jeopardize the security of the networks they are connected to) until they are decommissioned.
Information collected about citizens for the purposes of targeted advertising is an ongoing issue of concern. With IoT devices in the mix, we are bound to have cases in which data collected from IoT sensors within our homes will be leveraged for marketing, contributing to intrusive privacy violations. Health information, traditionally trapped within instruments and records in hospitals, is also now being collected by consumer devices that may be vulnerable to tampering. Such data may be utilized for research and stored in multiple locations in the cloud, thus increasing the probability of exposure.
Areas around the world are starting to leverage the concept of the smart city to serve their citizens efficiently. The combination of industrial- and consumer-grade IoT devices that empower these cities will introduce risk and open citizens up to privacy and security attacks that were previously limited to online spaces.
With respect to travelling to Mars and making our machines more intelligent, humankind faces great potential for triumph as well as great peril from threat agents—including superintelligent machines. As we make progress in the fields of space travel, interspace communication, and machine intelligence, we are going have to put a lot of thought into how to secure these platforms early on, because vulnerabilities in these areas could lead to the loss of human lives and curtail our ability to colonize other planets.
The ultimate goal of the cybersecurity profession is to enable connected technology as securely and swiftly as possible, and this enablement must begin with informed predictions of upcoming scenarios of attacks such as the ones discussed in this chapter.
