Threat intelligence and ransomware
Understand the latest ransomware delivery methods, use the latest network indicators, and detect the latest behavioral indicators.
 Internet peering map (source: Niau33 via Wikimedia Commons)
Internet peering map (source: Niau33 via Wikimedia Commons)
Threat intelligence is a great guide to responding to the continuous evolution we see attackers undergoing today as part of their criminal schemes. Simply put, by understanding the types of attacks your peers and partners are experiencing, you can learn about what you should be looking for on your network and in your information systems.
Most digital extortionists will blanket groups of similar companies to extract the ransoms through a fear-based system that allows them to raise their ransom requests over time, before moving on to the next set of targets. This is because they often share similarities in applications and platforms, therefore making it easier to get more targets.
By building trusted information-sharing circles, you can both give and get intelligence from industry peers that is anonymous and provides solid meta data useful in detecting the indicators of an attack.
Understanding the Latest Delivery Methods
Most ransomware only requires one thing to take action on your network—end-user interaction. An attacker can craft a single email with a malicious link or attachment and send out 100,000 emails in hopes that they get a 1% click-through rate.
Let’s do the math on this really quick: 500,000 emails with a click-through rate of 1% means 5,000 potential infections. According to Microsoft, in 2014, 23% of computers connected to the Internet were unprotected.1 This would mean that out of 5,000 clicks, 1,150 potential infections would occur. According to Symantec’s most recent report, the average ransom request is $679.2 Roughly 50% of people will pay the ransom, which means a take of $390,425 per email campaign. Given that the investment to get started is minimal, as noted in Chapter 4, we’re talking about anywhere from 500-2,000% ROI. Imagine getting that kind of return on a stock with a limited investment in time and money. It’s certainly better than robbing banks! These number are somewhat dated, but you get the point.
Since the primary means for spreading these is via email, digital criminals will use the names and logos of well-known organizations when creating their scam emails. This will increase a user’s likelihood of trusting the email and clicking the link. You should be suspicious of emails from shipping companies, postal services, and the like that require you to download a file to confirm receipt of an item or to follow a link to track the item. Another common method is tax return spam using common logos and personal information to make people think they’re getting a refund or are being audited. Another method we have seen gaining traction is invoice spam and credit card rewards spam.
The most common attachments use PDFs, but early in 2016, an increase in Windows script files (WSF) as a means to bypass traditional email filtering was observed. These WSF files are launched on a Windows system just like an executable. They are often included in zipped folders appearing to contain a Word doc. Once this zipped file is extracted, the WSF execution occurs and the ransomware once installed. JavaScript files are also posing as .doc files as well, which makes for ransomware that is potentially executable on a number of platforms, not simply Windows computers, but Macs and Linux boxes as well.
As more people become aware and effective at blocking these file types, the criminals will move to other techniques and file types.
One of the other common infection methods is via exploit kits like the Neutrino or Angler exploit kits (see Figure 1-1). Exploit kits are a way that criminals deliver malware through malvertisement networks.
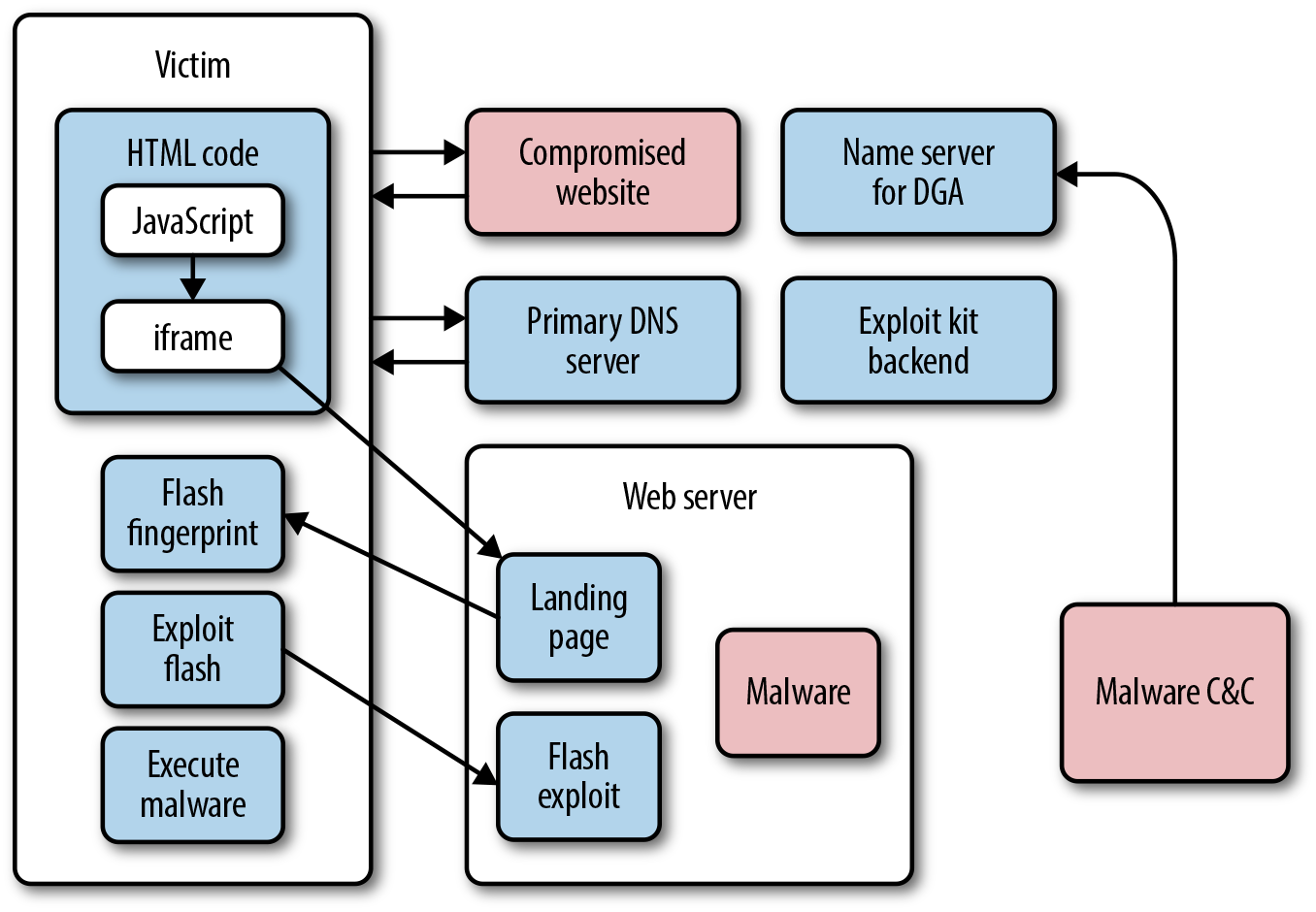
The Neutrino exploit kit works via multiple layers of evaluation of a system and exploitation of vulnerabilities in the applications installed:
- An end user will browse through to a web server that has been compromised.
- The web server will make contact with the Neutrino infrastructure to perform a variety of checks for CVE2014-892, etc., and, will then use the outcome of these checks to generate a malicious JavaScript. Inside this JavaScript there are URLs that are dynamically generated by the backend system using DGAs.
- The client’s browser will process and decode this malicious JavaScript. This script validates a number of client-side settings, including the browser version. If the browser version matches one that is exploitable by the criminal’s tools, a cookie will be dropped on the victim device and an
iframetag will be processed client-side. - The
iframetag causes the browser to generate another request to a URL that leads to the Neutrino kit landing page. - Once the victim lands on the Neutrino kit page, an object tag is delivered to the client’s browser, which will cause the client to load Flash player and use it to play a specific SWF.
- The browser accepts the instruction and downloads the SWF.
- Adobe Flash plays the downloaded file and exploits vulnerabilities, including:
- If the exploitation is successful, the ransomware will download and begin its execution process.
Note
Additional Neutrino Resources
For more information on the Neutrino exploit kit, see Luis Rocha’s detailed analysis.
Using the Latest Network Indicators
By properly researching all of the delivery methods, many of which are described in Part III of this book, about the major families of ransomware, you can get a baseline understanding of the network indicators you should begin looking for. Understanding the nature of the communications between the various ransomware families and their command-and-control channel will help you better understand what infection you have and if there are counter measures you can deploy. Additionally, by taking advantage of these indicators, you can potentially stop the spread of the infection to other systems.
For example, the Cyber Threat Alliance has a list of IPs and URLs associated with the command-and-control channels used in CryptoWall campaigns (see Table 1-1). This data is incredibly useful because you can use this information to block communication to and from the IPs and domains when you are attempting to interrupt the key exchanges. Keep in mind that data is in constant flux.
| Country | IP | URL | Date First Seen |
|---|---|---|---|
| Brazil | 186.202.127.240 | http://conectcon.com/evYR0G.php | 12/25/2015 |
| China | 118.193.164.218 | http://damozhai.com/aJPK4y.php | 12/25/2015 |
| France | 51.254.207.61 | http://naimselmonaj.com/QoYx31.php | 12/25/2015 |
| France | 51.254.207.181 | http://zemamranews.com/jxke9u.php | 12/25/2015 |
| France | 91.216.107.152 | http://abenorbenin.com/jcMISv.php | 12/25/2015 |
| France | 193.37.145.25 | http://tmp3malinium.com/7DSCmu.php | 12/25/2015 |
| France | 193.37.145.75 | http://engagedforpeace.org/R4uGnH.php | 12/25/2015 |
| France | 193.37.145.133 | http://ipanema-penthouse.com/lxUs6S.php | 12/25/2015 |
| Germany | 185.15.244.81 | http://sudatrain.net/De1uQF.php | 12/25/2015 |
| India | 43.225.55.90 | http://meaarts.com/bMUmqv.php | 12/25/2015 |
| India | 103.21.59.171 | http://rationwalaaa.com/QOPYrs.php | 12/25/2015 |
| India | 103.21.59.171 | http://safepeace.com/_QXEd6.php | 12/25/2015 |
| India | 103.21.59.171 | http://sparshsewa.com/5a8CTM.php | 12/25/2015 |
| India | 103.21.59.171 | http://spideragroscience.com/cWo1T2.php | 12/25/2015 |
| India | 111.118.215.210 | http://icanconsultancy.org/nm9Eul.php | 12/25/2015 |
| Indonesia | 103.23.22.248 | http://handmade.co.id/m2MEnC.php | 12/25/2015 |
| Japan | 183.90.232.29 | http://immigrating.xsrv.jp/5OUAvK.php | 12/25/2015 |
| Netherlands | 185.63.252.62 | http://primemovies.net/z6Hfan.php | 12/25/2015 |
| Russia | 78.110.50.124 | http://asistent.su/F3eRnj.php | 12/25/2015 |
| Russia | 90.156.201.70 | http://noblevisage.com/2qs9Rr.php | 12/25/2015 |
| Russia | 195.208.1.155 | http://pretor.su/ZLoNyf.php | 12/25/2015 |
| Russia | 195.208.1.155 | http://xn--e1asbeck.xn--p1ai/7xSCFU.php | 12/25/2015 |
| Spain | 185.86.210.42 | http://descargar-facebook-messenger.com/UjZHsJ.php | 12/25/2015 |
| Turkey | 94.73.147.150 | http://snocmobilya.com/XqDZ4I.php | 12/25/2015 |
| Turkey | 94.73.151.78 | http://sadefuar.com/xdqHcr.php | 12/25/2015 |
| Ukraine | 176.114.1.110 | http://reanimator-service.com/Y1U5s7.php | 12/25/2015 |
| United States | 63.135.124.25 | http://suttonfarms.net/gqd1aw.php | 12/25/2015 |
| United States | 69.73.182.77 | http://konstructmarketing.com/Ml63Pu.php | 12/25/2015 |
| United States | 104.28.17.110 | http://vlsex.net/O4vH1A.php | 12/25/2015 |
| United States | 104.218.54.211 | http://bookstower.com/bmrWeQ.php | 12/25/2015 |
| United States | 173.233.76.118 | http://droidmaza.com/eHViNt.php | 12/25/2015 |
| United States | 192.169.57.44 | http://therealdiehls.com/K3_J96.php | 12/25/2015 |
| United States | 192.185.35.88 | http://forexinsuracembard.com/j97S0E.php | 12/25/2015 |
| United States | 205.144.171.80 | http://centroinformativoviral.com/k6dYbZ.php | 12/25/2015 |
| United States | 208.91.199.77 | http://befitster.com/Bfv30s.php | 12/25/2015 |
| United States | 209.54.52.223 | http://tamazawatokuichiro.com/TkCs3y.php | 12/25/2015 |
| Vietnam | 112.78.2.45 | http://nobilighting.com/eX8yjr.php | 12/25/2015 |
By creating proactive measures on your DNS servers, firewalls, and proxies and by preventing communications to, or resolution for, the IP addresses and URLs, you can lock down the communication channels and interrupt the kill chain associated with the ransomware.
Additional network indicators to look for that will help you move up the kill chain include email attachment and subject lines.3
| Type | Indicator |
|---|---|
| Email subject | ATTN: Invoice_J-<8-digits> |
| Attachment filename | invoice_J-<8-digits>.doc |
Each type of indicator has a specific purpose in interrupting the chain of events that lead to infection and ultimately extortion. Collecting known subject lines, filenames, and file hashes will help you prevent the initial compromise. By blocking these files at the SMTP gateway, scanning all inbound files, and preventing macros from being executable on your end-point devices you are taking the first step in prevention.
The next place to interrupt the communications is in the outbound command-and-control communications by leveraging the channels used for redirection to malspam websites and known command-and-control channels. In Figure 1-2 you will see samples of traffic from the Zepto variant of Locky, this traffic is the type of network communications you should look to interrupt.4
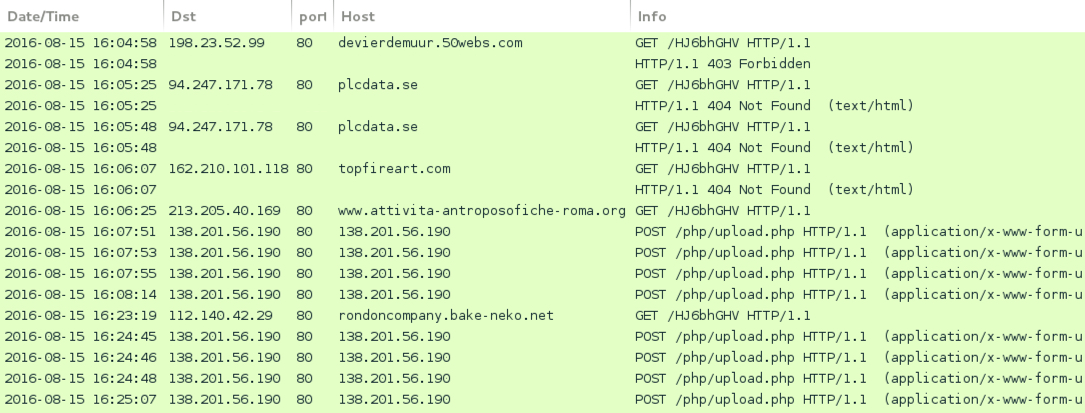
However, compiling, maintaining, and updating the lists of known C2 channels in your various technologies is a gruesome task, as there is not a single repository for all network communications with every known ransomware command-and-control channel, email subject line, SHA256 hash, and attachment filename. This means you need to develop practices that leverage multiple sources of intelligence and extract it into a system by which you can visualize the indicators in a meaningful manner. You must also begin to look for patterns in the data, as well as develop a better understanding of the easiest sources of this information. You’ll find that there are a number of new (and established) vendors on the so-called threat intelligence platform (TIP)-based approach to intelligence analysis on the market. Each of the platforms has strengths and weaknesses, and though we are talking about them in general, your investigation into the platforms is best done by the team who will be working with the platform directly. Anomali, ThreatQ, and ThreatConnect are a few of the vendors out there marketing TIPs that will not only correlate open source data, from places like the CTA, Zeus Tracker, and the like, but will also integrate with many of the closed source or premium feeds, like those from the FS-ISAC, Retail-ISAC, Symantec, FireEye, and McAfee.
Detecting the Latest Behavioral Indicators
The other indicators you need to be concerned about are behavior-based indicators. Based on your understanding of user behavior, you can intercept activities associated with a particular ransomware variant and stop the destructive activities they attempt.
Figure 1-3 shows how CryptXXX leverages multiple processes to modify the file and watch for abnormal system behavior that halts and restarts the encryption if you are attempting to detect basic encryption on a system using traditional scanning and processes analysis methods.5 This means that you need to evaluate the process logs to determine the history of processes on the infected system and look for this type of behavior, which is ostensibly a meta analysis of the processes on the system.
By looking at the behavior of processes on your end-user systems, you can determine login and and resource access attempts and use this information to determine if a system has been compromised, how the compromise is attempting to traverse the network, and in what manner it is attempting to contact network drives or files to begin the encryption process.
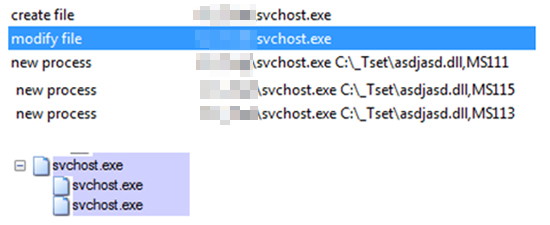
Baselining your users’ behaviors is how you develop this understanding. First, you need to know who has access to what specific resources on your network. By leveraging the group policy features of Windows, you can determine which systems have access to which resources and when those resources get accessed. Additionally, in each user’s profile, you can set baseline working hours and then compare those baselines to real-time behavior. By collecting these metrics over time and continuously comparing the results of your collection to the established baselines, you will be able to identify outliers. These become investigation points for further analysis. Products like Darktrace Threat Visualizer will help you identify these outliers and automatically respond to these shifts.
User Behavior Analytics
This type of detection is formally known as user behavior analytics (UBA) and is an area of focus in the cybersecurity industry, particularly in the realm of insider threat. UBA is a unique way to detect, alert on, and possibly block a ransomware attack. Instead of looking for specific behaviors, UBA relies on determining what is out of the ordinary for a given system or network. For example, it is unusual for an application to access all of the files on a system in rapid succession, but that doesn’t mean that this behavior doesn’t happen. It could be a backup program accessing those files. UBA looks at not only the behavior but the behavior in the context of that specific workstation. If the backup program accesses all of the files outside of business hours every day, but if this file is accessing all of the files at 11:34 a.m., it should be flagged.
By searching for anomalous behavior specific to that system or network, UBA detection systems can identify behavior that is outside of the norm in a statistically significant manner. A user may visit 10 different websites during his lunch break on most days, but during fantasy football draft period, that number jumps to 25, which is unusual behavior but does not necessarily indicate a threat. On the other hand, if that user visits the same website 50 times in the span of an hour, that should be flagged.
In the end, UBA builds profiles of specific users and can report deviations that are statistically significant. Because ransomware causes systems to behave abnormally, UBA systems have a better chance than a lot of other security tools of detecting and alerting on new or unknown strains of ransomware.
Summary
Threat intelligence must be gathered from a variety of sources. You must also know your network and the users on it in order to identify abnormal behavior. Applying these indicators helps you minimize the effects of an attack and in some cases prevent attacks altogether.
1Jeffrey Meisner, “Latest Security Intelligence Report Shows 24 Percent of PCs are Unprotected,” Official Microsoft Blog, April 17, 2013.
2Symantec Security Response, “REPORT: Organizations must respond to increasing threat of ransomware,” Symantec Official Blog, July 19, 2016.
3Brandon Levene, Micah Yates, and Rob Downs, “Locky: New Ransomware Mimics Dridex-Style Distribution,” Palo Alto Networks Blog, February 16, 2016.
4“2016-08-15 – Zepto variant Locky malspam,” Malware-Traffic-Analysis, August 8, 2016.
5Jaaziel Carlos, Anthony Melgarejo, Rhena Inocencio, and Joseph C. Chen, “Will CryptXXX Replace TeslaCrypt After Ransomware Shakeup?” TrendLabs Security Intelligence Blog, May 20, 2016.