2Cyber Security – An Introduction to Assessment and Maturity Frameworks
There are security implications that result from our incorporating computer automation, or cyber, into business systems and industrial control systems that underpin almost everything we do. Assessing these cyber systems, to ensure resilience, is performed through a number of well‐known frameworks to develop an initial understanding, or baseline, of our current system security levels.
Assessments often begin with an asset prioritization, a “Crown Jewels Analysis1” (MITRE) being one example, with more detailed evaluations developed from this initial structure. Figure 2.1 provides an example “Enterprise Risk Analysis” structuring designed to perform this high‐level prioritization, with detailed process modeling showing system dependencies for structural evaluation. Component‐level assessment, or penetration testing, is then used at the technology level to inventory the system’s architecture.
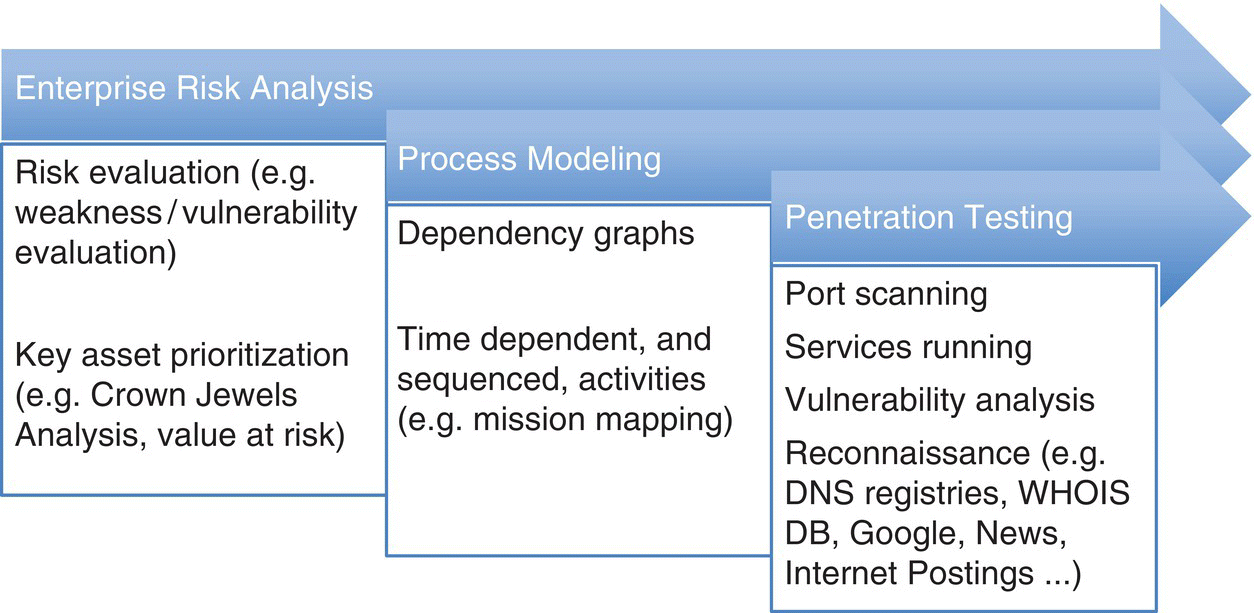
Figure 2.1 Assessment levels – enterprise risk, process modeling, and vulnerability analysis.
As shown in Figure 2.1, network evaluation spans from an overall key asset prioritization to specific network components. This can include using dependency or attack graphs, during process modeling, to highlight specific scenarios.
2.1 Assessment Frameworks
The standard Confidentiality, Integrity, and Availability (CIA) information ...
Get An Introduction to Cyber Modeling and Simulation now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

