Chapter 3. Tuning
This chapter talks about how BEEP sessions get lawyered-up. The term “lawyered-up” is just an expression that some of us use for adding security to a plain vanilla BEEP session. When a BEEP session starts out, you get whatever security properties are provided by the underlying transport service. In most cases, this means that your traffic is unencrypted and unauthenticated. Now, maybe that’s okay for your environment, and if that’s the case, make sure that you’re dosing properly with your meds. If not, then BEEP gives you a way of fixing that. It’s called “tuning,” which is the official term for the process of giving a newly-created BEEP session the security properties you want, as shown in Figure 3-1.
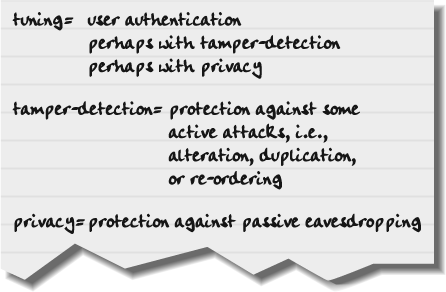
Figure 3-1. The tuning precept
In BEEP, sessions are tuned for two things:
Transport privacy
User authentication
Sometimes you can accomplish both of these simultaneously; in other cases, you have to take care of privacy before authentication. It’s all a function of the security technologies you have available. Don’t worry, we’ll explain the details later on. The one thing you must understand is that BEEP’s view of security is entirely protocol-centric—you’re still responsible for what happens to the data before and after it gets sent. (In other words, tuning doesn’t help with sloppy coding such as buffer overflows.)
Before we talk about the details of tuning, we have to ...
Get BEEP: The Definitive Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

