Scenario 8-1: Defining IOS Commands to View DoS Attacks in Real Time
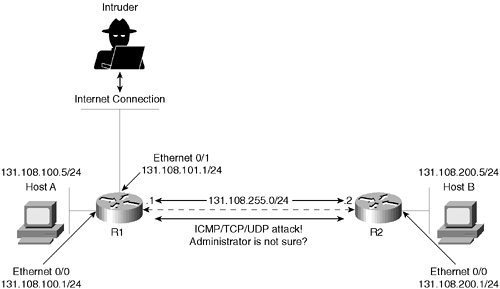
| Q1: | Figure 8-3 displays a typical two-router topology with an external connection to the Internet via R1.
Figure 8-3. Two-Router Network Attacked by External Intruder
In this scenario, a Cisco IOS router is subjected to ICMP, TCP, or UDP IP packets. The network administrator is not sure of what type but notices the log file that is buffered to the Router R2 has just increased from 1 MB to 2.5 MB in less than 5 seconds. What can be done to characterize the traffic and detect the type of denial-of-service attack? |
Get CCIE Security Exam Certification Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.