Understanding Threats to Your Wireless Security
As you read in Chapter 1, wireless infrastructures are very susceptible to attack and being breached. In this section, you'll learn about the various components that, when tabulated, represent a threat matrix to your wireless network.
The threat matrix is simply a list of threats that may jeopardize your business. By listing the threats and ranking their viability, you can determine where to shore up your systems.
In the fictional setup shown in Table 10-1, the “X” represents the level of threat, and the dash means no threat is present.
Table 10-1: Sample Threat Matrix for Wi-Fi
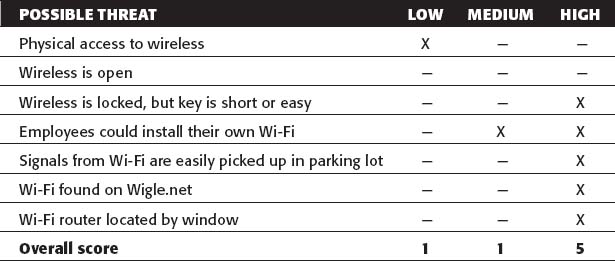
As you can see, this matrix results in a score of “5” in the “High” category, and, thus, this fictional setup is at a high risk of being breached.
Depending on your business, you will obviously design a different threat matrix. For example, if you are in a medical business in the United States, the requirements of the Health Insurance Portability and Accountability Act (HIPAA) and the more stringent requirements of the Health Information Technology for Economic and Clinical Health (HITECH) Act appear in your threat matrix. Another area of concern might be financial data, such as credit or debit card transactions. In the last few years, one high-profile retailer was breached through a wireless system, and millions of card numbers (and dollars) were stolen.
Get CMS Security Handbook: The Comprehensive Guide for WordPress®, Joomla!®, Drupal™, and Plone® now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

