Chapter 3. What Are the Threats?
“By heaven, I’ll make a ghost of him that lets me.”
Hamlet, William Shakespeare
It’s 5 p.m. Friday, the last night of your on-call rotation as an incident investigator. You’ve just shut down for the weekend, and as you’re about to leave the office, your mobile buzzes with a text message: “IT-OPS: Sev5 Possible production FTP server compromise. Ongoing conf call.” You jump on the telephony bridge to learn that some sysadmins were troubleshooting a failed FTP server on one of their externally facing hosts. After remotely rebooting the server, they were unable to log into the host. A sysadmin in the datacenter connected to the local console of the host and encountered a large text box like the one shown in Figure 3-1.
The instructions detail how to wire the criminals the $5,000 ransom via Western Union, MoneyGram, or the now defunct Liberty Reserve, along with amateurish assurances that the cryptography could not be broken, and that they’ll take no mercy on your data. Immediately, thoughts start running through your head as you jump into the incident lifecycle: How did the host get infected with ransomware? Is our customer data encrypted? Are there other infected or similarly vulnerable hosts? What customer-facing services are now offline with this host out of commission? Why didn’t I leave work 10 minutes earlier?
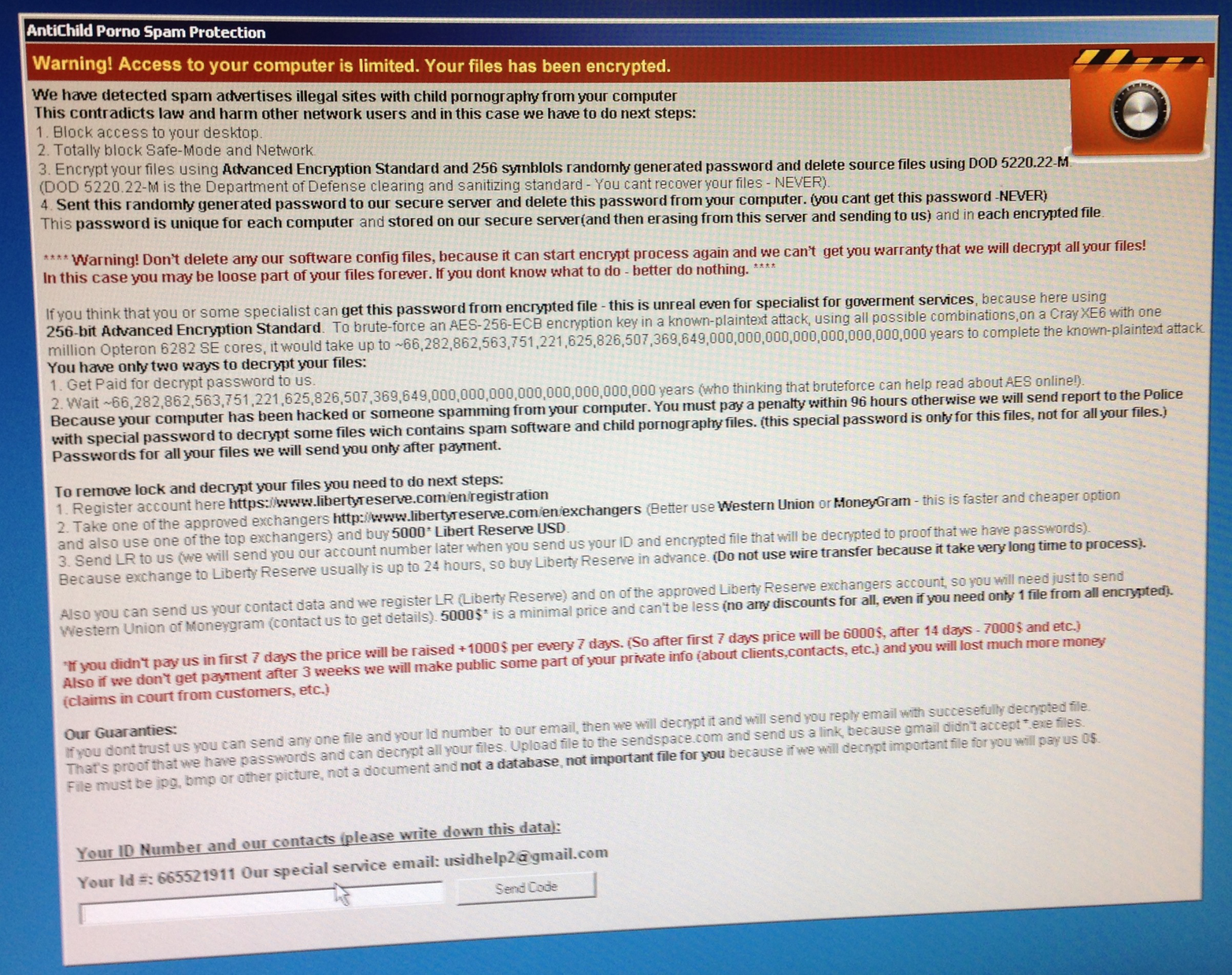
Figure 3-1. Ransomware screenshot ...
Get Crafting the InfoSec Playbook now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

