How to Configure Encryption
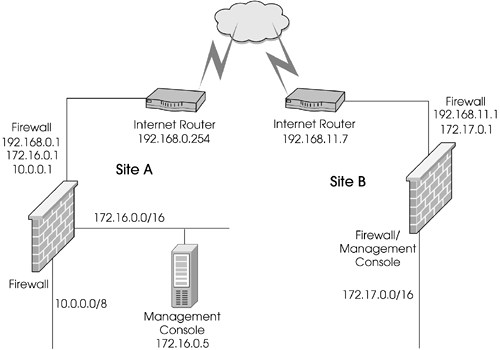
As you will find, the steps in configuring encryption are very similar regardless of which encryption scheme you use. Throughout this section, I refer to the proposed VPN setup in Figure 11.1.
Figure 11.1. Sample VPN configuration
NOTE!
 | As noted previously in the book, I treat 192.168.x.x as routable address space even though it is generally not considered routable per RFC1918. |
Planning Your Deployment
You need the following information when planning a VPN based in FireWall-1:
Which hosts and/or networks the remote site ...
Get Essential Check Point™ FireWall-1® NG: An Installation, Configuration, and Troubleshooting Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

