You may want to view the list of IP endpoints that your system is communicating with. To achieve this, you can navigate to the Statistics tab and select Conversations, as shown in the following screenshot:
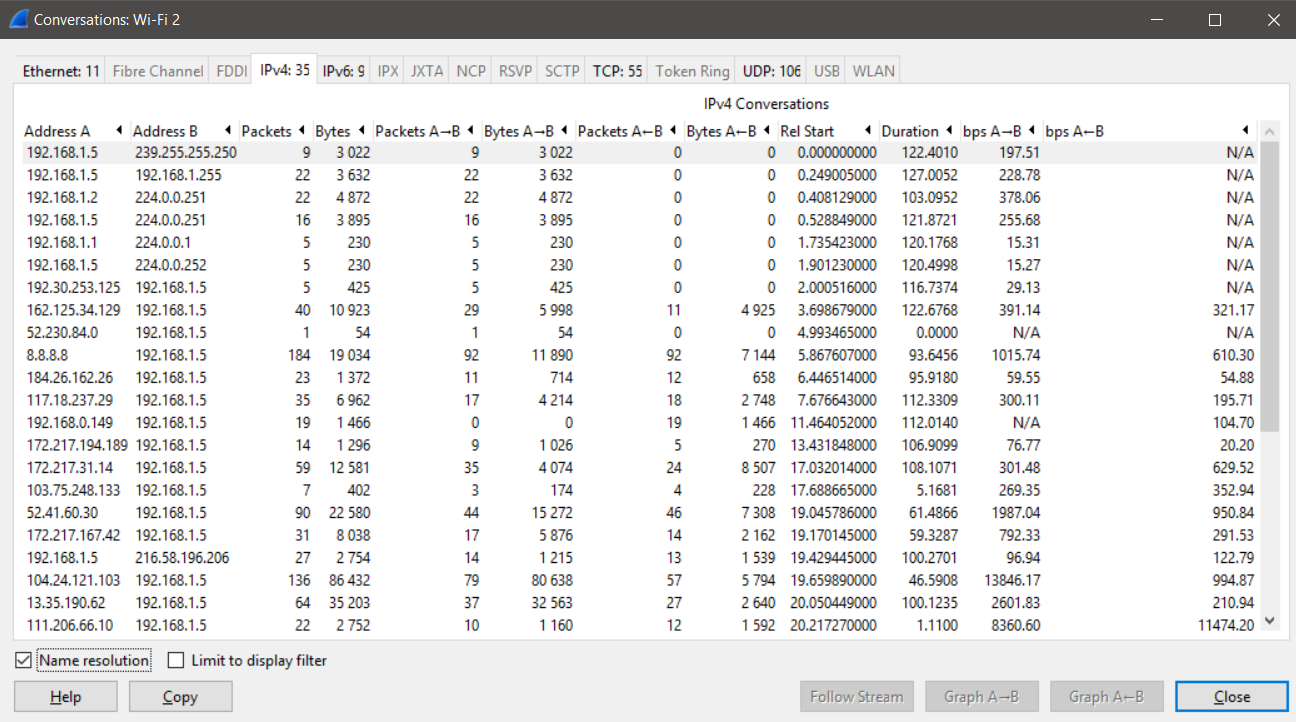
We can see that we have a variety of endpoints that are having conversations, the number of bytes transferred between the endpoints, and the duration of their data exchange. These options become extremely handy when you want to investigate malicious traffic and identify the key endpoints that are being contracted. Additionally, we can see that most of the conversations in the preceding screenshot involves ...

