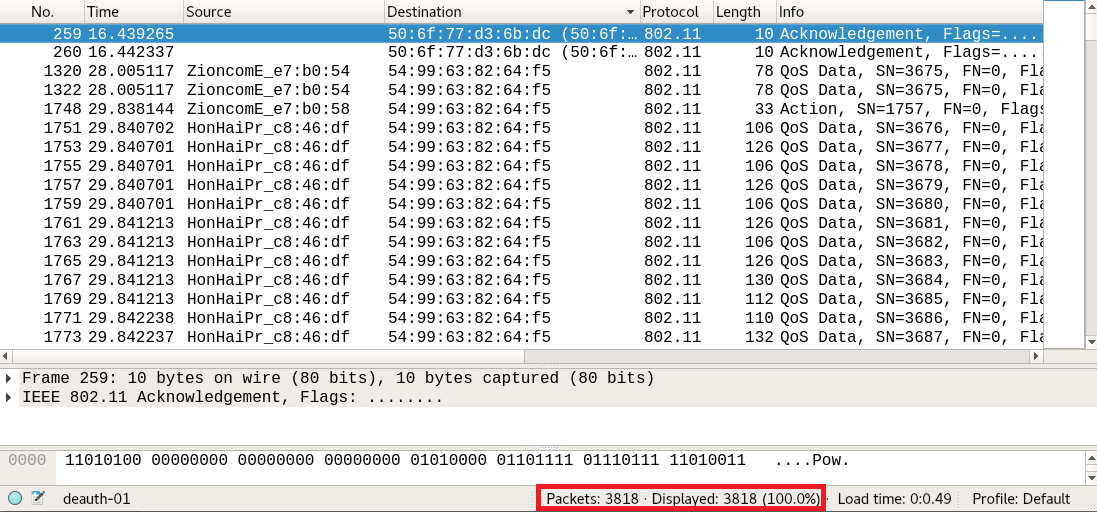
In this section, we will analyze a sample capture file covering the details of an attack on a WPA2 network. Loading the file in Wireshark, we can see that we have 3,818 packets, as shown in the following screenshot:
Let's clear the noise by filtering out only management frames using the wlan.fc.type filter and the value 0x0, as follows:
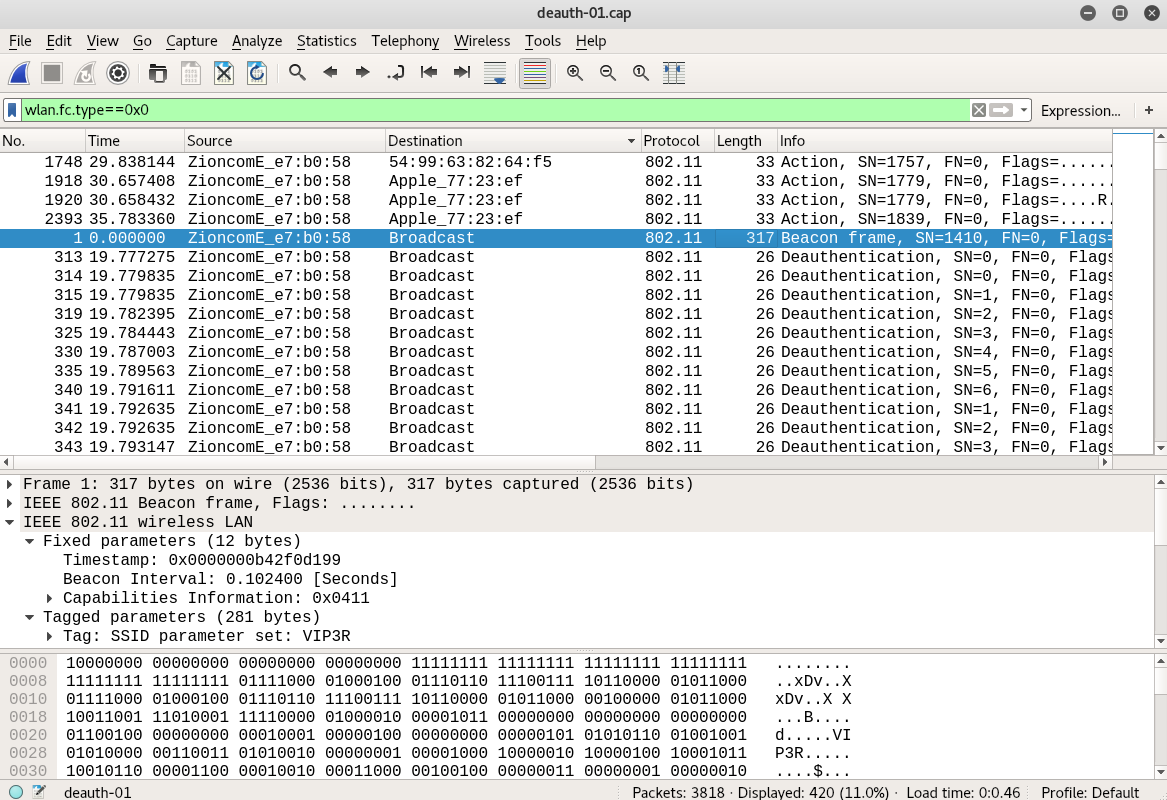
We can see that we are left with only 420 packets, and we can also see plenty of deauthentication packets in the screenshot. Let's find out which device got affected by ...

