WEP 101
To truly understand the problems with WEP, we must first develop an understanding of how WEP works in its currently implemented form (Figure 3.1).
Figure 3.1. WEP encipherment.
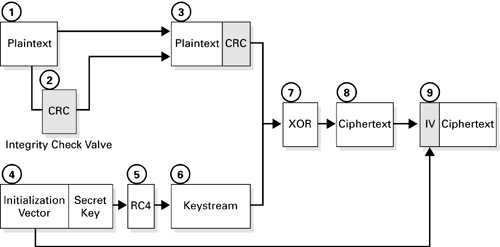
The encryption process always begins with a plaintext message that we want to protect. First WEP performs a 32-bit cyclic redundancy check (CRC) checksum operation on the message. WEP calls this the integrity check value and concatenates it to the end of the plaintext message. Next, we take the secret key and concatenate it to the end of the initialization vector (IV). Plug this IV + secret key combination into the RC4 Pseudo-Random Number Generator (PRNG) and it ...
Get How Secure Is Your Wireless Network? Safeguarding Your Wi-Fi LAN now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

