Validate Existing Security Infrastructure
Solutions in this chapter:
Introduction
We begin the process of securing the VoIP infrastructure by reviewing and validating the existing security infrastructure. Addition of VoIP components to a preexisting data network is the ideal opportunity to review and bolster existing security policy, architecture, and processes.
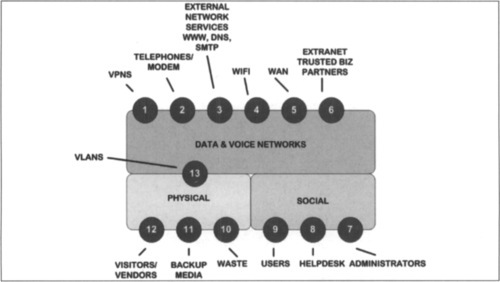
One way of visualizing the components of a given security architecture is to use Figure A.1, which graphically shows a number of network security interfaces.
Get How to Cheat at VoIP Security now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

