Pre-Authentication
The original Kerberos 4 protocol was susceptible to offline dictionary and brute-force attacks, as we’ll see in Chapter 6. This vulnerability stems from the fact that the KDC issues an encrypted TGT to any client for any principal (given that the requested principal exists in the Kerberos database). Since the KDC happily provides a ticket encrypted with the principals’ secret key to any requestor, an offline attack can be mounted to determine the principal’s secret key. This vulnerability is exacerbated by the fact that users typically choose poor passwords.
To make this attack more difficult, Kerberos 5 introduces pre-authentication (see Figure 3-11). Pre-authentication requires that requestors prove their identity before the KDC will issue a ticket for a particular principal. There are several types of pre-authentication defined by the Kerberos Clarifications document. However, only the encrypted timestamp (PA-ENC-TIMESTAMP) pre-authentication method is commonly implemented.
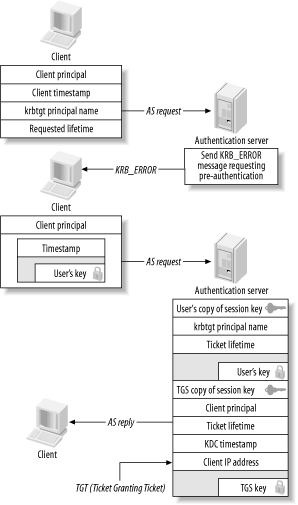 |
Pre-authentication is controlled by KDC policy. If a user attempts to acquire initial tickets through the AS exchange, but the KDC requires pre-authentication, then the KDC will send a KRB_ERROR message instead of an AS_REP in reply to the client’s AS request. This KRB_ERROR message tells the client that pre-authentication is required. The client ...
Get Kerberos: The Definitive Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

