This is the Title of the Book, eMatter Edition
Copyright © 2008 O’Reilly & Associates, Inc. All rights reserved.
Locking Down Windows
|
393
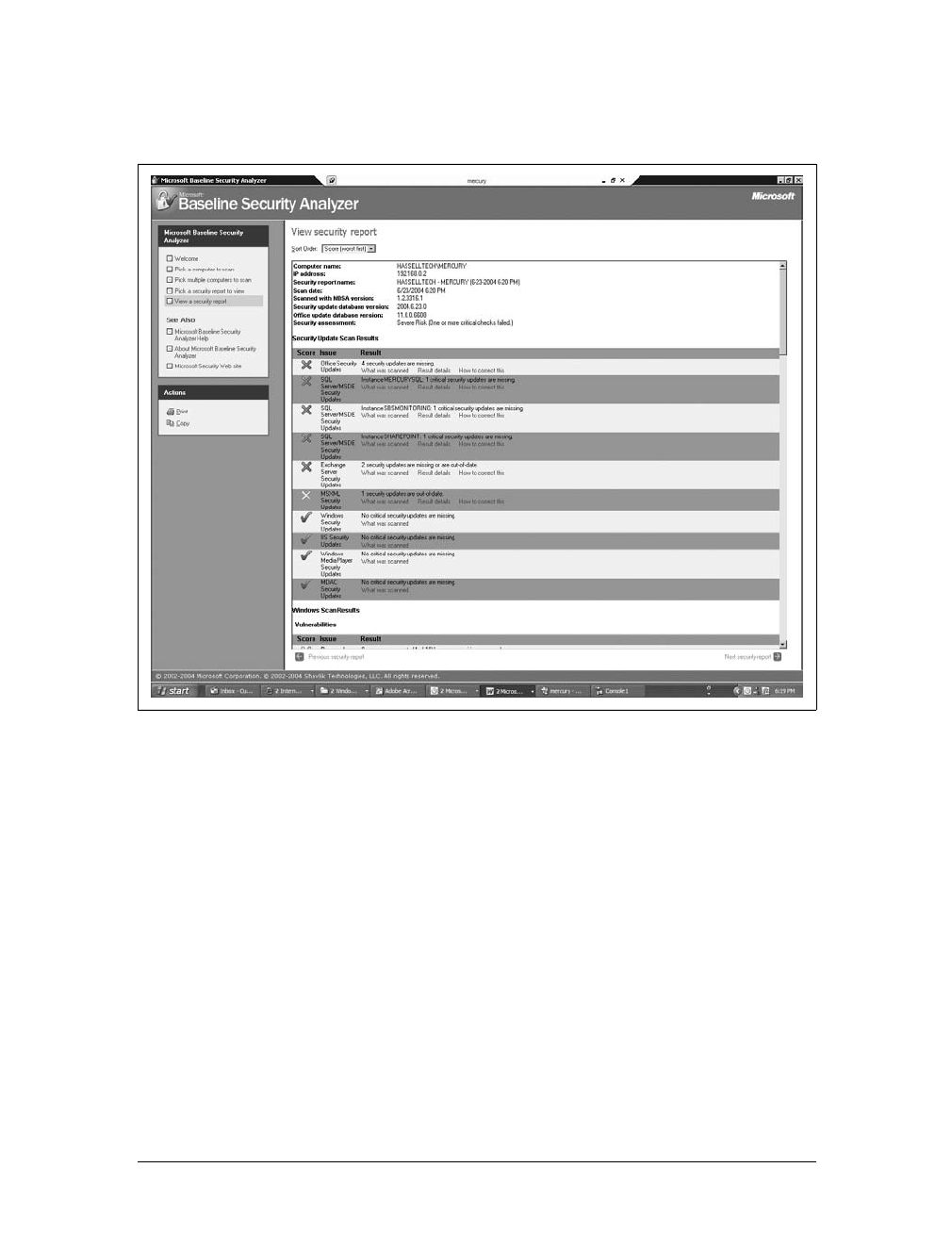
6. When the scan is complete, you’ll see the View security report screen. A sample
screen is shown in Figure 7-11.
7. You can see each issue the scan identified, how serious the issue is, and a link to
information on how to correct it.
A suggestion about security strategy: I recommend you use the MBSA before apply-
ing your security templates or SCW policies to know what issues to address, and
then run it once again after your templates or SCW policies have been applied and
tested to in order to identify what might have slipped through the cracks.
Locking Down Windows
Multi-user systems are security holes in and of themselves. The simplest systems—
those used by only one person—are the easiest ones to secure because there’s much
less diversity and variance of usage on the part of one person than there is on the
part of many. Unfortunately, most of our IT environments require multiple user
accounts, so the following section focuses on some prudent ways to lock down
Figure 7-11. MBSA scan results
Get Learning Windows Server 2003, Second Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

