Chapter 8. Configuring Microsoft ISA Server Firewall Policy
In this chapter, we focus on the Microsoft ISA Server firewall policy, specifically the system policy, firewall policy, and access rules. We explain how policies are processed and how you can easily export and import your policy configurations. The second half of the chapter focuses on publishing, allowing external sources to access your internal network resources securely and safely.
Understanding How ISA Server Processes Traffic
ISA Server inspects traffic by referring to three sets of rules in the order shown in Figure 8-1.
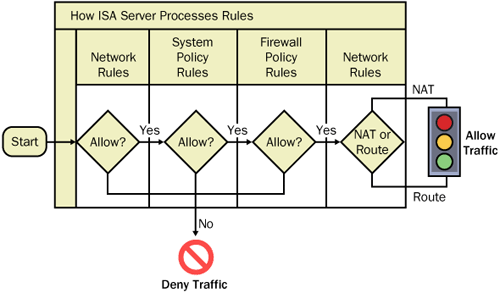
Figure 8-1. ISA Server processes network rules, system policy rules, ...
Get Microsoft® Internet Security and Acceleration (ISA) Server 2004 Administrator's Pocket Consultant now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

