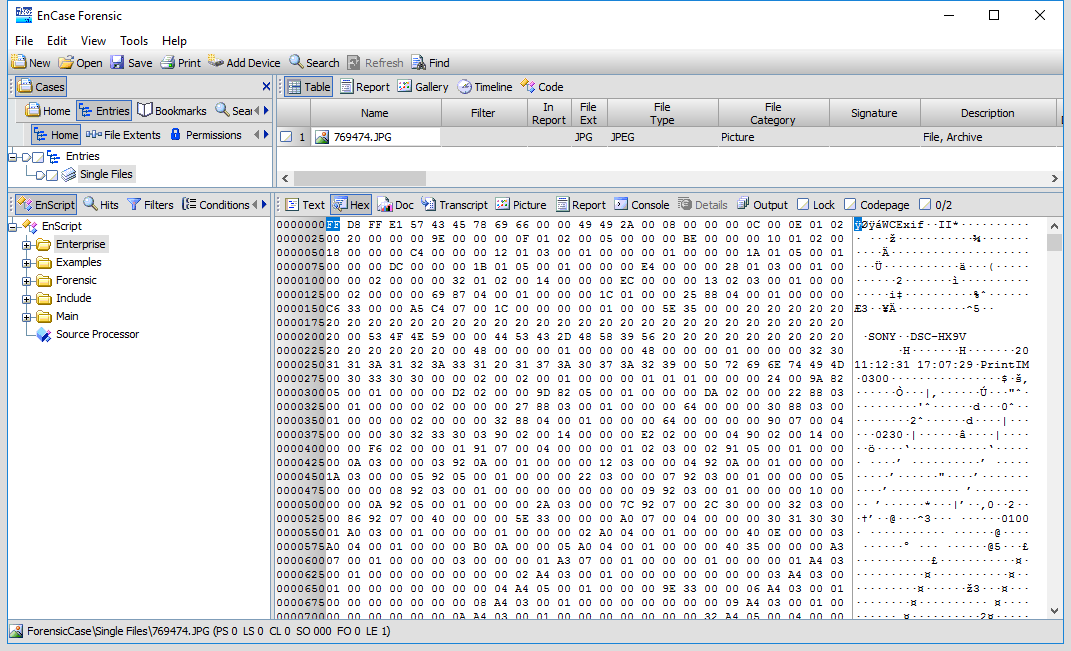
With the open case, we can look at the hex of a photo of interest to confirm we can see the EXIF header within the file. Following this header are the raw values processed by the script. With a good candidate identified, let's look at how we can configure EnCase to run the script.
Under the View menu, we select the File Viewers option. This opens a tab listing the available viewers. The instance of EnCase we used does not have any viewers and so we must add any we wish to use first.
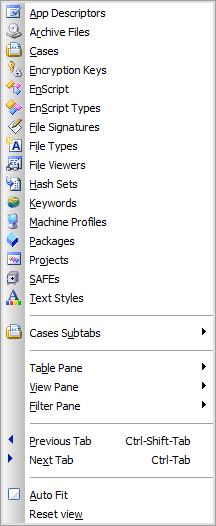
In this tab, right-click on the top-level ...

