Secure—Basic Architecture
This architecture (FIGURE 3-4) continues to build upon the typical architecture, adding the proxy servers for user access (that is, IMAP or POP).
Figure 3-4. Proxy Configuration With SMTP Relays and Firewall
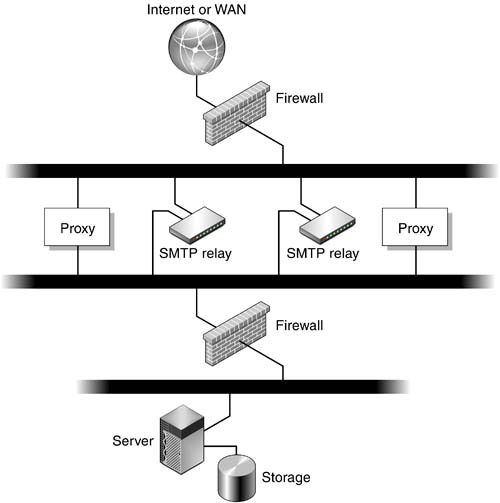
The addition of these proxy servers extends the protocols through the firewall securely. Users must authenticate to these servers first, then they are proxied to the messaging server and only the messaging server.
Note
This configuration does not address all aspects of messaging security such as SSL, Secure Multipurpose Internet Mail Extensions (SMIME), or encrypted file system. Some of these methods are discussed ...
Get Sun™ ONE Messaging Server: Practices and Techniques for Enterprise Customers now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

