9.4 ICD V: Plain Text IP Layer Peer-to-Peer
In this section, we cover a number of protocols that are needed for the plain text IP layer peer-to-peer communications. These protocols optimize the use of resources over the HAIPE encrypted core network. These protocols are explained in Sections 9.4.1–9.4.5.
9.4.1 TCP Proxy over HAIPE
Please review Appendix 3.A where a transport layer hybrid ARQ over HAIPE was presented. This hybrid ARQ over HAIPE compresses the packet payload and generates redundancy packets to overcome packet loss from the encrypted core path. A TCP proxy over HAIPE can use this technique, as shown in Figure 9.7. In the figure, the TCP proxy over HAIPE has three main components: the compressor/decompressor, the Reed–Solomon (RS) encoder/decoder, and the flow control component. Standard TCP proxy14 has only the flow control component. Let us consider the following two cases to conceptualize how this proxy works.
Figure 9.7 Plain text IP layer TCP proxy elements.
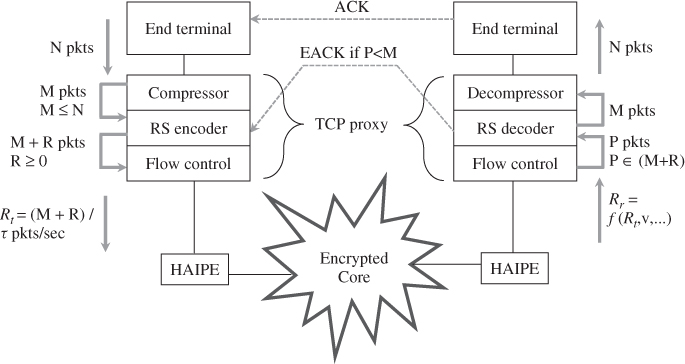
First, consider the case where retransmission is not necessary. Packet flow between end-terminals is conducted as follows:
Get Tactical Wireless Communications and Networks: Design Concepts and Challenges now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

