Chapter 1. Step 1: Getting In
Before I get too far, let’s talk about how to connect to a Linux system in the first place. If you have an actual physical machine, you can use the console. In today’s day and age, this isn’t likely. If you are running VMs, you can use the VM software’s console mechanism.
But most Linux systems run OpenSSH, a Secure Shell service, which creates an encrypted terminal connection via TCP/IP, typically to port 22. So, obviously, if you are connecting to an off-premise system, the appropriate firewall holes have to be in place on both sides. This allows you to connect from anywhere you want to work.
On Windows, you generally use PuTTY to establish SSH sessions with Linux systems. You typically need credentials as well, either from that sticky note your boss found, or preferably via your company’s secure credentials management system.
You also could connect using public/private key pairs, but that is beyond the scope of this report.
When you start PuTTY, it looks like Figure 1-1.
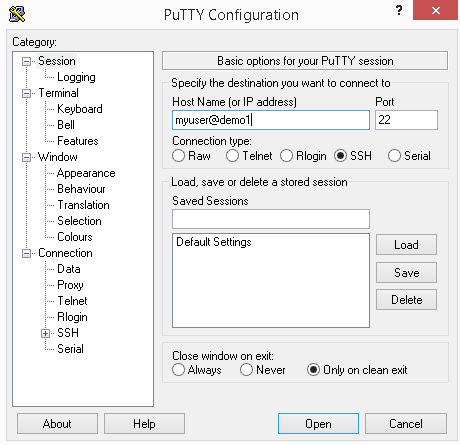
Figure 1-1. PuTTY prompt
You typically type in a user ID (in this example, myuser),
followed by the at sign, @, and then the system’s domain name or IP
address (in this example, demo1).
When you click the Open button, if this is the first time you are connecting via SSH to a remote system, you will receive a warning similar to the one in Figure 1-2.
Figure 1-2. PuTTY alert
Simply ...
Get Ten Steps to Linux Survival now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

