Security Threats
As show in Figure 8-1, there are several forms of security threats to wireless networks. For example, hackers can steal information from a company, obtain unauthorized access to applications, and even disrupt operation of the network.
Figure 8-1. Threats to Wireless Network Security Include Passive Monitoring, Unauthorized Access, and Denial of Service (DoS)
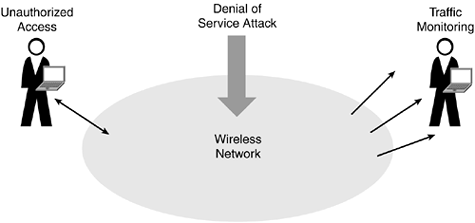
Traffic Monitoring
An experienced hacker, or even casual snooper, can easily monitor unprotected wireless data packets using tools such as AirMagnet and AiroPeek, which fully disclose the contents of wireless data packets. For example, snoopers can monitor all transactions ...
Get Wireless Networks first-step now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

