Chapter 4
Concepts in Action – Part 1
In this chapter, we will merge together all the topics we discussed in the previous chapters. If you recall, we discussed the Proxim application, through which we looked at data encryption. We will analyze its source code in detail here. We will also work through some examples of applications that require and use permissions.
The Proxim Application
The Proxim project should have a structure similar to that depicted in Figure 4-1
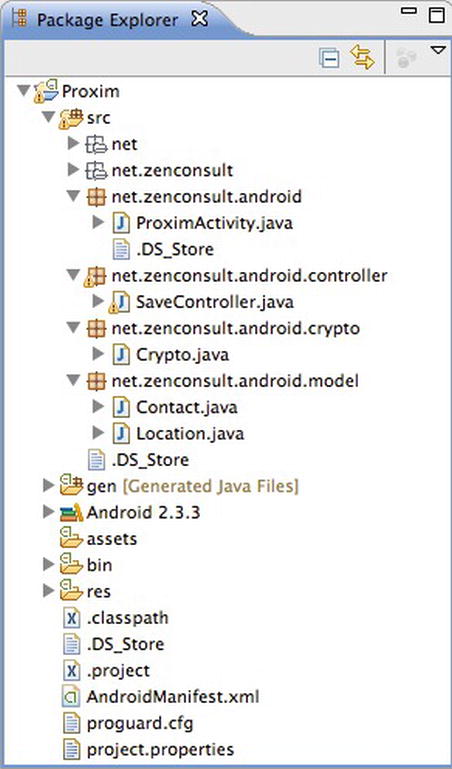
Figure 4-1. The Proxim Application structure
Let’s start with the Activity, which is where your programs usually will start (see Listing 4-1). In the Activity, we are creating ...
Get Android Apps Security now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

