Chapter 2Android Security Design and Architecture
Android is comprised of several mechanisms playing a role in security checking and enforcement. Like any modern operating system, many of these mechanisms interact with each other, exchanging information about subjects (apps/users), objects (other apps, files, devices), and operations to be performed (read, write, delete, and so on). Oftentimes, enforcement occurs without incident; but occasionally, things slip through the cracks, affording opportunity for abuse. This chapter discusses the security design and architecture of Android, setting the stage for analyzing the overall attack surface of the Android platform.
Understanding Android System Architecture
The general Android architecture has, at times, been described as “Java on Linux.” However, this is a bit of a misnomer and doesn't entirely do justice to the complexity and architecture of the platform. The overall architecture consists of components that fall into five main layers, including Android applications, the Android Framework, the Dalvik virtual machine, user-space native code, and the Linux kernel. Figure 2.1 shows how these layers comprise the Android software stack.
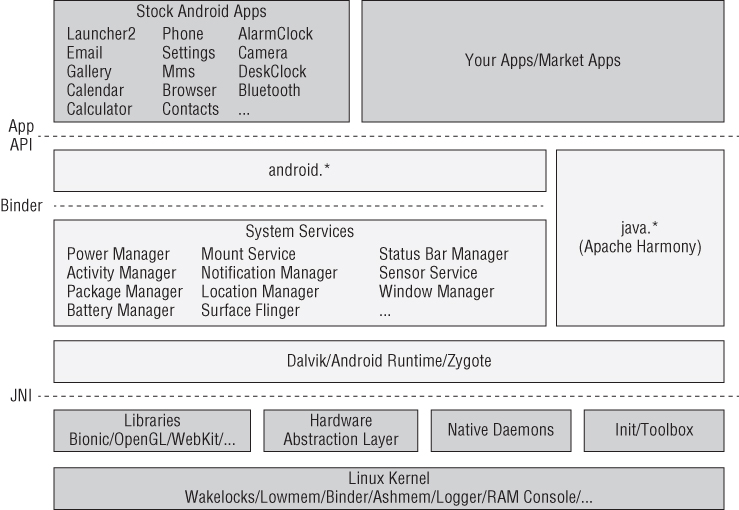
Figure 2.1 General Android system architecture
Source: Karim Yaghmour of Opersys Inc. (Creative Commons Share-Alike 3.0 license) http://www.slideshare.net/opersys/inside-androids-ui
Android applications ...
Get Android Hacker's Handbook now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

