CHAPTER 23
Special Algorithms for Protocols
23.1 MULTIPLE-KEY PUBLIC-KEY CRYPTOGRAPHY
This is a generalization of RSA (see Section 19.3) [217,212]. The modulus, n, is the product of two primes, p and q. However, instead of choosing e and d such that ed ≡ 1 mod ((p - 1)(q - 1)), choose t keys, Ki, such that
![]()
Since
![]()
this is a multiple-key scheme as described in Section 3.5.
If, for example, there are five keys, a message encrypted with K3 and K5 can be decrypted with K1, K2, and K4:
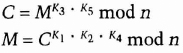
One use for this is multisignatures. Imagine a situation where both Alice and Bob have to sign a document for it to be valid. Use three keys: K1, K2, and K3. The first two are issued one each to Alice and Bob, and the third is made public.
- (1) First Alice signs M and sends it to Bob.
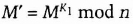
- (2) Bob can recover M from M′.
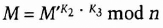
- (3) He can also add his signature.
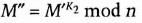
- (4) Anyone can verify the signature with K3, the public key. ...
Get Applied Cryptography: Protocols, Algorithms, and Source Code in C, Second Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

