Offensive security tools are often the same tools hackers use, but for different purposes. While hackers use these tools for malicious reasons, cyber security professionals use them to find vulnerabilities. Once the vulnerability is located, a defense is deployed to prevent exploitation of the network. Penetration testing is used to determine the weak points of a system or network. Penetration testing tools are often combined into operating systems like Kali Linux.
The following is a screenshot displaying the tools menu in Kali Linux:
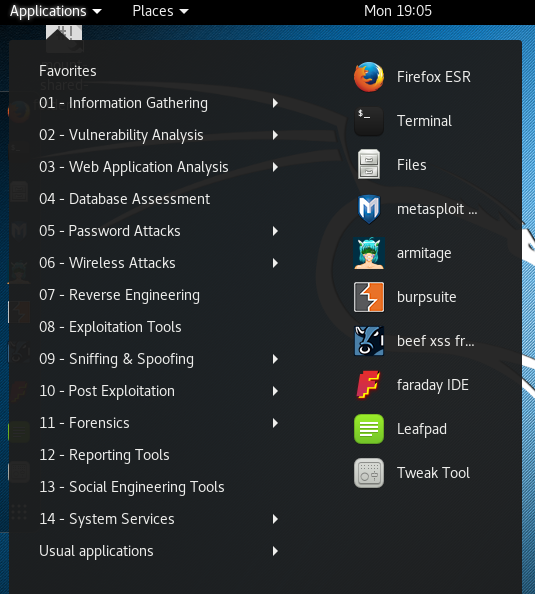
Pen testers often follow the five phases of ethical hacking to ...

