Attacking the firewall
Next, we want to attack the firewall, like we did earlier when we encountered the router. Our success will be determined by the administrator and how they have configured their environment.
We will use the Smoothwall and pfSense firewall that we created, and we will attack them from the external interface. We will use the same process we used against the router and see what we can discover when we go against the firewall. Our testing range is shown in the following diagram:
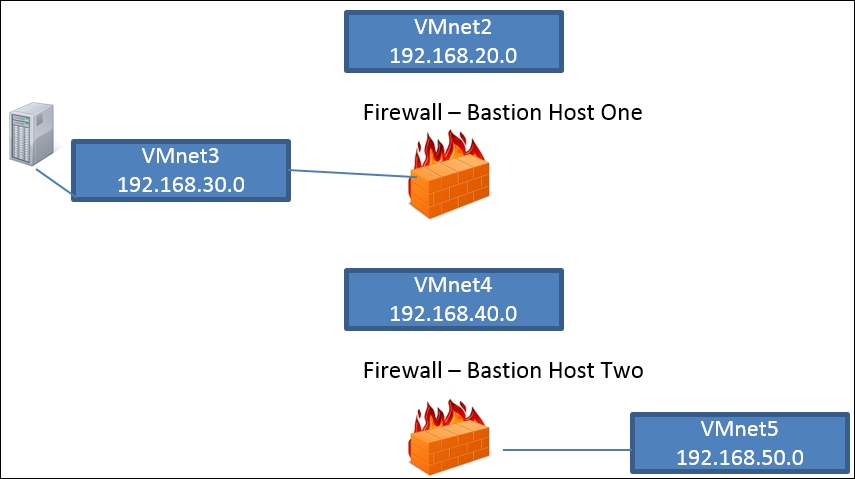
As the previous diagram shows, we will just concentrate on the external interface of the Smoothwall (Bastion Host One) and pfSense (Bastion Host Two) machine. ...
Get Building Virtual Pentesting Labs for Advanced Penetration Testing - Second Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

