Scenario 5-1: Configuring Cisco Routers for IPSec
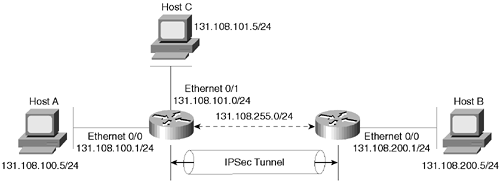
Figure 5-21 displays a simple two-router topology where traffic from network 131.108.100.0/24 is encrypted when it is sent to the remote network 131.108.200.0/24.
Figure 5-21. Scenario Topology
Example 5-21 displays the working configuration of R1 numbered from 1 to 31.
Example 5-21. R1's Full Configuration
1. version 12.2 2.hostname R1 3.enable password cisco 4.crypto isakmp policy 1 5. hash md5 6. authentication pre-share 7. crypto isakmp key CCIE address 131.108.255.2 8. crypto ipsec transform-set anyname esp-des esp-sha-hmac 9. mode transport 10.crypto map anyname1 1 ipsec-isakmp 11. set peer ... |
Get CCIE Security Exam Certification Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

