Appendix C. Memory Tables Answer Key
Chapter 2
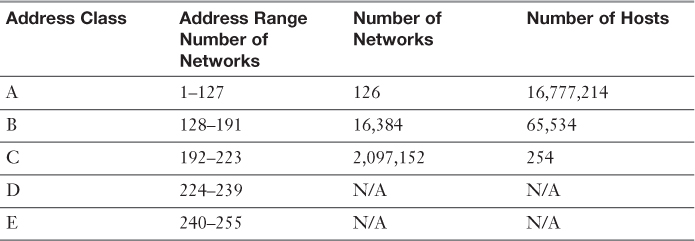
Table 2-3 IPv4 Addressing
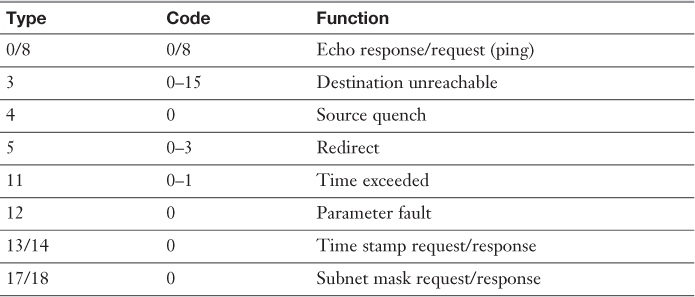
Table 2-5 ICMP Types and Codes
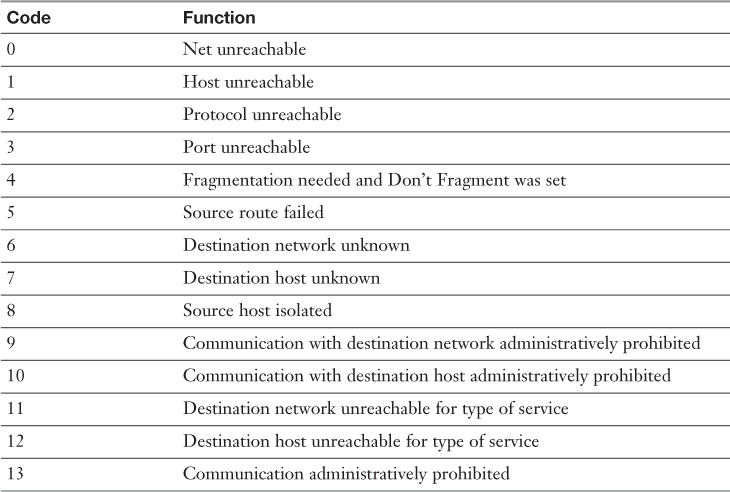
Table 2-6 Some Common Type 3 Codes
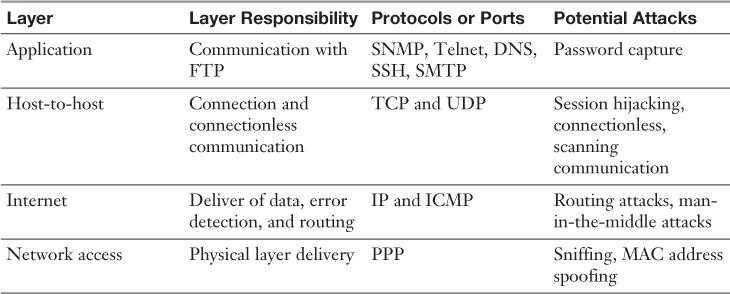
Table 2-8 Layers and Responsibilities
Chapter 3
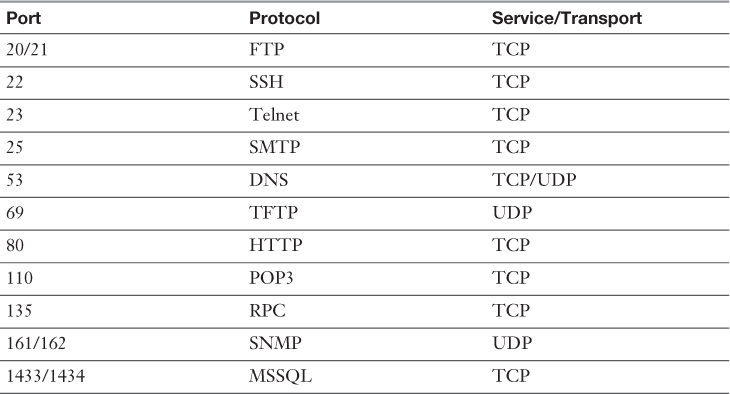
Table 3-5 Common Ports and Protocols
Table 3-7 The Seven ...
Get Certified Ethical Hacker (CEH) Cert Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

