Chapter 5. Implementing High Availability with VPNs 309
5.2 Test network design
As mentioned earlier in this book, the new version of VPN-1/Firewall-1 has
the ability to synchronize the state tables between two or more Firewall
modules. The state synchronization allows for the preservation of active TCP
sessions at the point of a failover. This also allows for the preservation of
active VPN sessions between a SecuRemote client and the VPN-1/Firewall-1
module. The installation and basic configuration of AIX 4.3.3,
VPN-1/Firewall-1, and HACMP is the same as that described in earlier
chapters. This section will document the changes to the configurations.
5.2.1 Test network topology
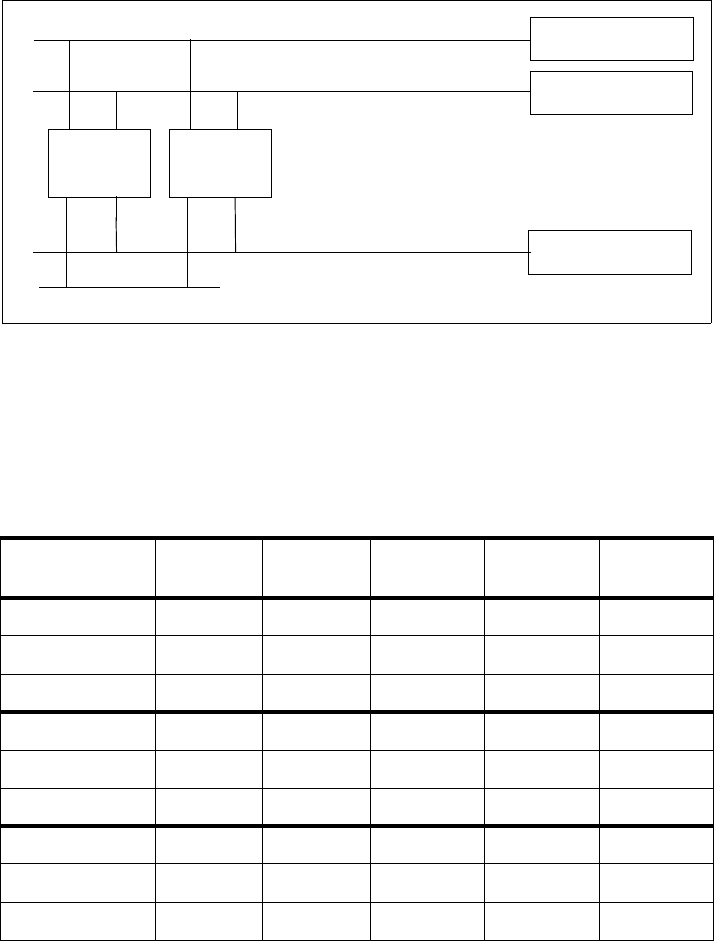
Figure 115 on page 310 shows the network plan for our VPN-1/Firewall-1 and
HACMP testing. As before, our test environment consists of two RS/6000
machines (called cpfw1 and cpfw2). There are four networks attached to the
firewalls:
• fw_ext, which represents the “non-secure” or external network. This could
be the Internet, for example.
• fw_dmz, which is a demilitarized zone (DMZ) for publicly accessible Web
and FTP servers.
• fw_man, which is a firewall management LAN that connects just the two
firewalls. In our scenario, we used a single RJ45 crossover cable attached
to the on-board ethernet adapters of the two firewalls.
• fw_int, which represents the internal network, for example, a company’s
intranet.