General Conclusion
The scenario of a Chinese cyber-threat feeds into the discourse held in the circles of security and defense in many countries. It intersects with the scenario of the threat against critical infrastructures. For example, Congressman Mike Rogers, Chairman of the House Permanent Select Committee on Intelligence and a former FBI agent, is the proponent of a law bill entitled “The Cyber Intelligence Sharing and Protection Act”1, the aim of which is to “facilitate information sharing, interaction, and collaboration among and between federal, state, local, tribal, and territorial governments, cybersecurity providers, and self-protected entities.”2 He supports this project because of the need to protect America from the threat of cyber-attacks from China, Russia and Iran against the country’s infrastructures. Others maintain that China is conducting massive-scale cyber-espionage operations. According to the US Office of the National Counter Intelligence Executive (ONCIX): “America’s annual costs due to cyber espionage could be as high as $400 billion a year [...] Chinese actors are the world’s most active and persistent perpetrators of economic espionage.”3
The topics and arguments interweave with one another to form the scenario presented in the graph below.
Figure C.1. The scenarios (and their components) of the Chinese cyber-threat
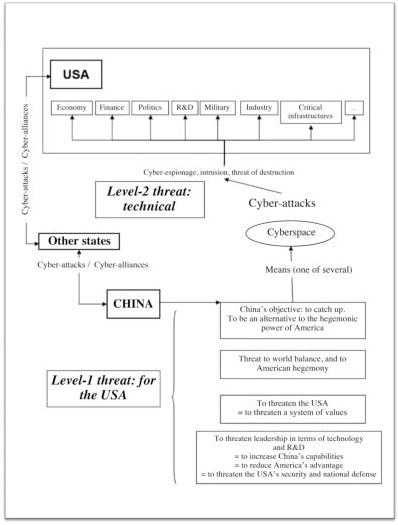
Yet to what extent are the argument ...
Get Chinese Cybersecurity and Cyberdefense now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

