Answers
This section contains the answers to the exercises and the Chapter review section in this chapter.
Exercise 7-1
The diagram should look similar to the following:
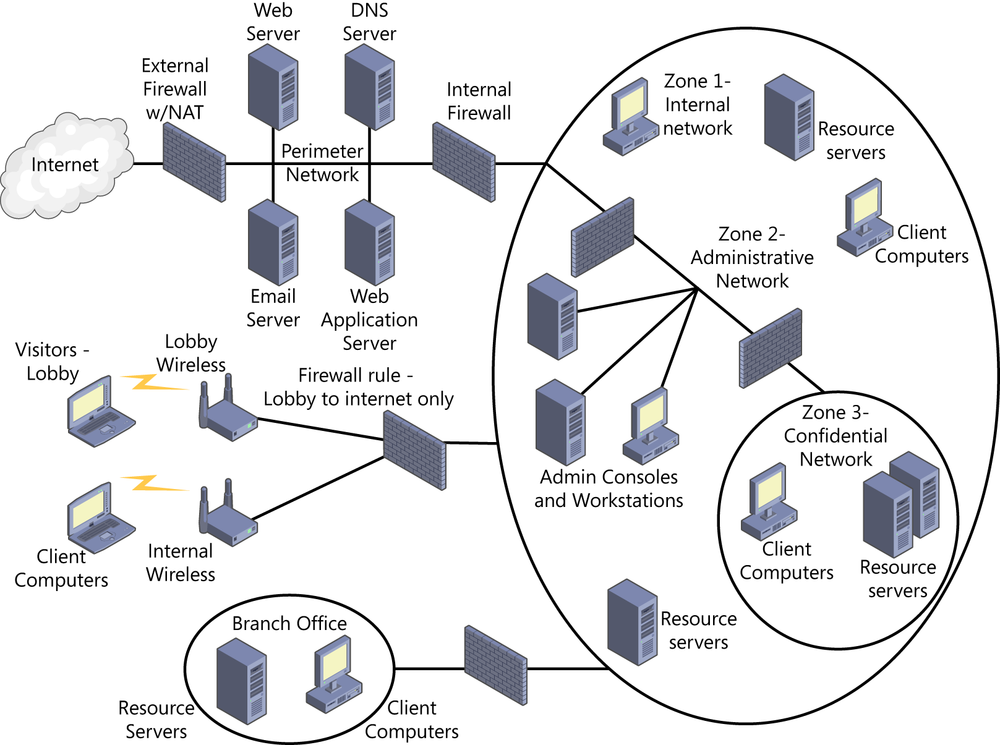
Figure 7-35. Exercise 7-1 network diagram
Exercise 7-2
At least two public IP addresses must be used on the public interface of the external firewall/NAT server. One address will be used to provide Internet access for internal users (many to one) and to provide public access to the web server, DNS server, and SMTP server using port forwarding (PAT), mapping port 80 and 443 to the private IP address of the web server, 53 to the private IP address of the DNS server, and 25 to the private ...
Get CISSP Training Kit now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

