6.8 ENIGMA KEY DISTRIBUTION PROTOCOL
Any system for distributing keys that allow the same daily keys K1, K2,… to be used by many military units is appealing, as it permits all entities to monitor all communications.
However, it has a serious cryptographic weakness, which is independent of the strength of the encipherment algorithm. If the ciphertext transmitted on the different links is monitored and arranged in rows
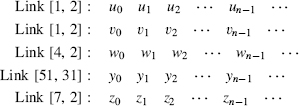
the ciphertext in each columns results from a monoalphabetic substitution and may be analyzed independently of the others. Shannon reasoned that 3–100 messages should be enough to recover the plaintext.
The German military understood the possibility of this vertical attack and developed an elaborate key management scheme to hopefully avoid any weakness. Each Enigma cipher machine came with a selection of rotors. In 1934, five rotors were distributed; the number was increased to eight in 1938 but the old rotors continuing to be used. The Enigma was a field encipherment system and the Germans had to assume the Allies would eventually capture a device. Security could not depend on keeping secret the rotor wirings as stated in Kerckhoff's Second Postulate
Compromise of the system should not inconvenience the correspondents.
In fact, the Polish Resistance captured an Enigma early in the war and a German submarine was forced to the surface, providing examples of rotors. ...
Get Computer Security and Cryptography now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

