Threat intelligence goes through a feedback cycle in order to keep pace with an ever-changing environment. While there are several methodologies that can place context around this challenge, one that is often utilized is the cycle of intelligence that is used by the US Department of Defense.
This cycle provides the framework and a starting point for organizations to incorporate threat intelligence into their operations:
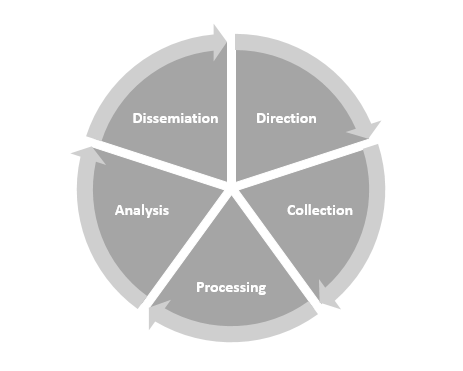
- Direction: Decision makers such as the CISO, information security personnel or incident response analysts set down what threat intelligence is required. In determining the requirements for intelligence, ...

