14 Endpoint Security and Compliance Management Design Guide Using IBM Tivoli Endpoint Manager
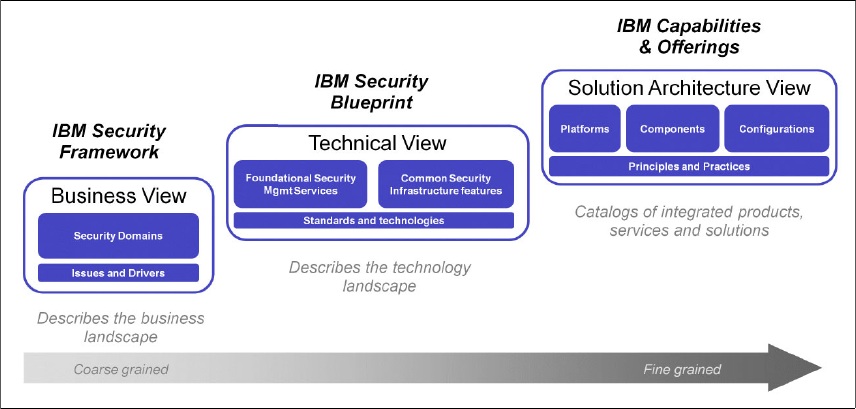
The left portion of Figure 1-3 on page 13 represents the IBM Security
Framework, which describes and defines the security domains from a business
perspective. It was covered in 1.2, “Introducing the IBM Security Framework” on
page 9.
The middle portion in Figure 1-3 on page 13 represents the IBM Security
Blueprint, which describes the IT security management and IT security
infrastructure capabilities needed in an organization. As discussed earlier, the
IBM Security Blueprint is product and vendor independent.
The right portion of Figure 1-3 on page 13 represents the solution architecture
views, which describe specific deployment guidance particular to an IT
environment. Solution architecture views provide details about specific products,
solutions, and their interactions.
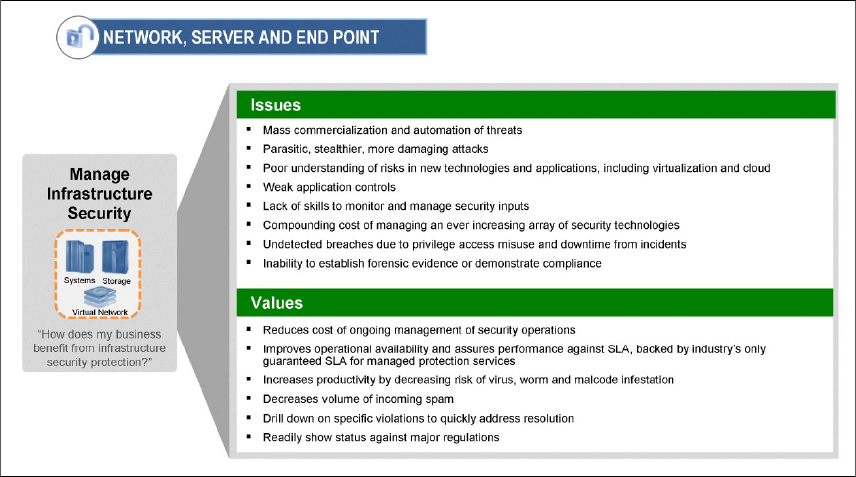
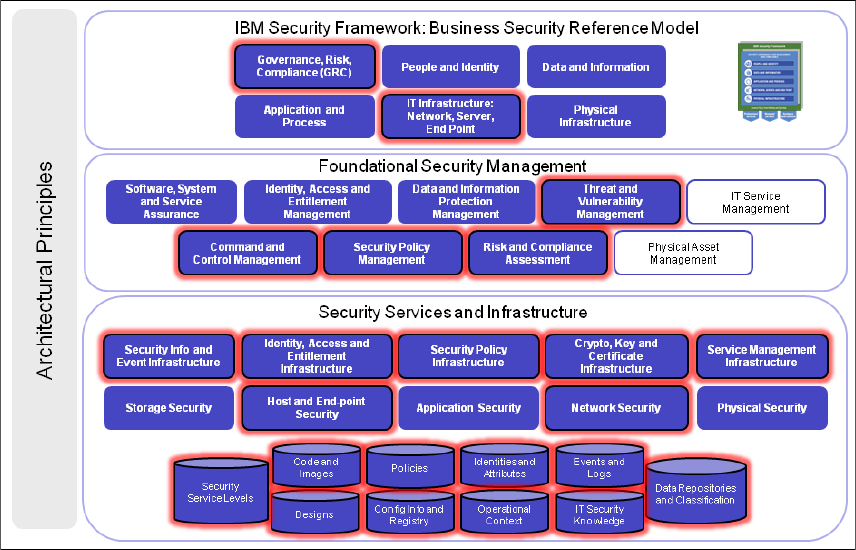
Figure 1-4 on page 15 highlights the components and subcomponents of the IBM
Security Blueprint that must be examined for every solution in the Network,
Server, and Endpoint security domain. In addition to the Foundational Security
Management Services, you can use the IBM Security Blueprint to determine the
Security Services and Infrastructure components by reviewing the component
catalogs for these Foundational Security Management Services. Each of these
components can then be assessed by determining whether each infrastructure
component is required to make a Foundational Security Management service
functional so that it can address the issues or provide a value associated with the
particular business security domain, in this case, Network, Server, and Endpoint.