Technology—Components
At this point, you should have a better idea of the technology products that exist and how they can be used together to provide multiple layers of protection. The question we need to answer is, “How do I get started, and what are some of the best practices in this area?” Figure 6-3 provides an overview of the hierarchy for implementing security technology.
Figure 6-3. Technology hierarchy of security.
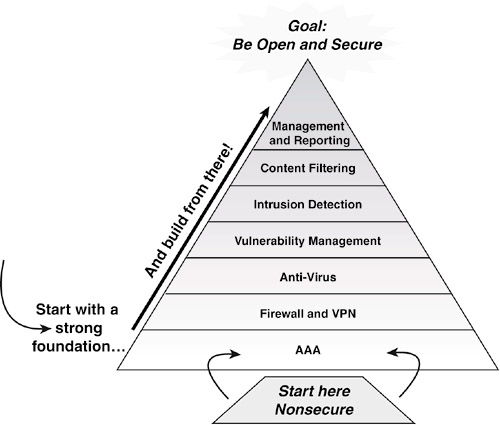
This hierarchy presents the relative priority for implementing each of these technologies at your company. You can use this hierarchy to help determine the priority for deploying products in your environment and to assist in ...
Get Executive Guide to Information Security, The: Threats, Challenges, and Solutions now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

