September 2012
Intermediate to advanced
512 pages
12h 41m
English
1. The following is pretty accurate:
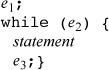
If e2 is not present in the for loop, the constant 1 is used for it in the above expansion (which would then be a nonterminating loop, unless something in statement terminates it).
Expressing a for loop in terms of a do loop is somewhat awkward, because the body of a do loop is always executed at least once, whereas the body of a for loop may not be executed at all, depending on e1 and e2. Nevertheless, the for loop can be expressed as follows.
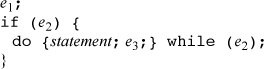
Again, if e2 is not ...