Chapter 6
Breaking into PCI-protected Areas
And when memory failed and written records were falsified-when that happened, the claim of the Party to have improved the conditions of human life had got to be accepted, because there did not exist, and never again could exist, any standard against which it could be tested.
—George Orwell
Most payment application vendors today sell PA-DSS validated software, and many merchants are PCI DSS compliant. It would be reasonable to assume that vulnerability areas which are protected already by PCI rules are in practice less vulnerable than others. However, even though this is true to a certain extent, it is not the case for all of them and there are security holes in PCI-protected areas.
PCI Areas of Interest
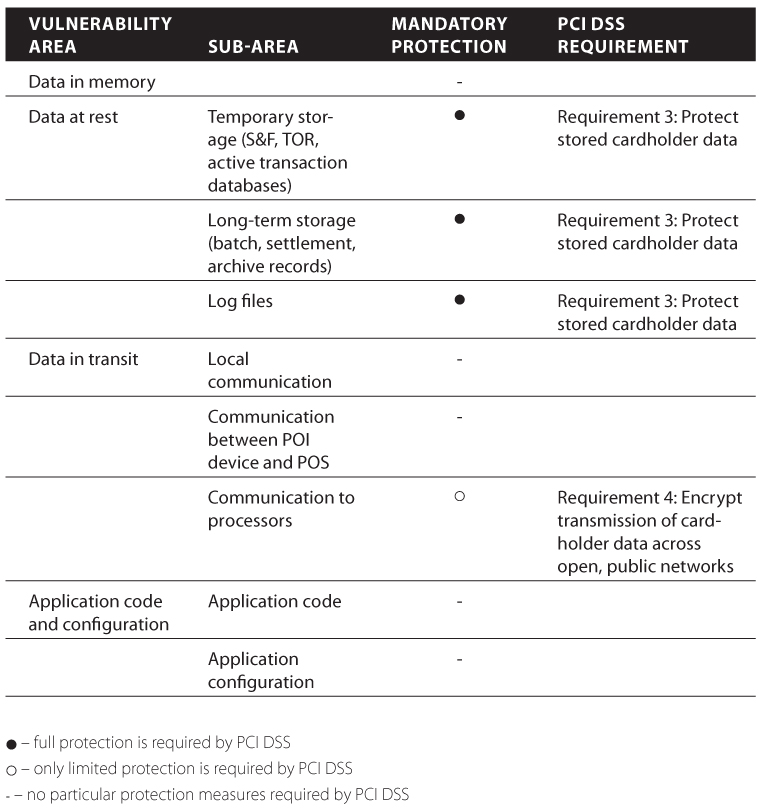
For mostly historical reasons, PCI security standards take care of very specific places where sensitive card data can be intercepted. If you take a look at the detailed review of PCI DSS and PA-DSS requirements provided in Chapter 3, you will be able to easily distinguish those two key zones: data at rest and data in transit. It is important to note that data-at-rest protection is supported by PCI almost in full, while data in transit protection is very limited and mostly ineffective inside the store or data center. These findings are summarized in Table 6.1.
Table 6.1 Payment Application Protection Provided by PCI
Data at Rest: The Mantra ...
Get Hacking Point of Sale: Payment Application Secrets, Threats, and Solutions now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

