CHAPTER 4
RFID READERS—REVIEW AND DESIGN
4.1 INTRODUCTION
Radio-frequency identification (RFID) is a wireless data capturing technique that utilizes radio-frequency (RF) waves for automatic identification of objects. RFID relies on RF waves for data transmission between the data-carrying device, called the RFID tag, and the interrogator [1, 2].
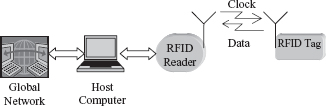
A typical RFID system is shown in Figure 4.1. An RFID system consists of three major components: a reader or interrogator, which sends the interrogation signals to an RFID tag, which is to be identified; an RFID tag or transponder, which contains the identification code; and middleware software, which maintains the interface and the software protocol to encode and decode the identification data from the reader into a mainframe or personal computer. The RFID reader can read tags only within the reader’s interrogation zone. The reader is most commonly connected to a host computer that performs additional signal processing and has a display of the tag’s identity. The host computer can also be connected via Internet for global connectivity/networking.
FIGURE 4.1 Block diagram of a typical RFID system.
RFID was first proposed by Stockman [1] in his landmark paper “Communication by Means of Reflected Power” in ...

