Chapter 13
Languages and Security: Safer Software Through Language and Compiler Techniques
Rahul Simha and Scotty Smith
13.1 Introduction
Developing secure software is a daunting task. Many tools and techniques have been created to alleviate the pressure of writing secure and efficient code. Some techniques were initially developed in the 1960s, whereas others are more recent developments. In the following chapter, we will be discussing defenses for different attacks on code and software systems. The defenses in this chapter will fall within the framework seen in Figure 13-1.
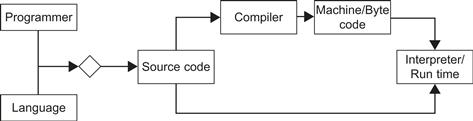
Figure 13-1 Software development cycle.
We discuss Watermarking in ...
Get Handbook on Securing Cyber-Physical Critical Infrastructure now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

