Let's load the PCAP in Wireshark as follows:
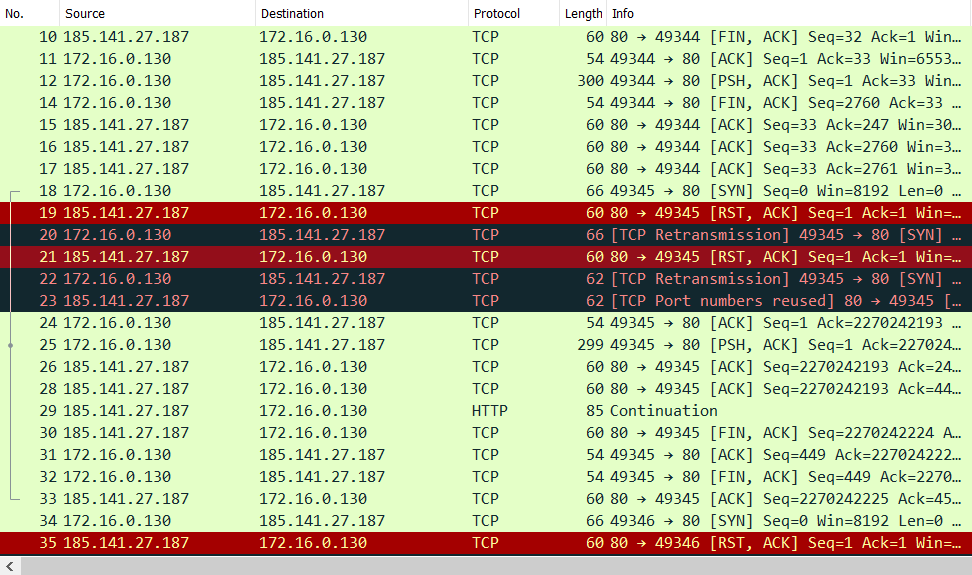
We can see that there is a lot of HTTP data present in the PCAP file. Let's add columns to display the full URI and User-Agent entries, and also filter the requests using the http.request.uri filter as follows:

The user-agent is quite important in malware communications, since they might not be the standard user-agents used by popular browsers. We can see we have Mozilla/4.08 (Charon; Inferno) as the user-agent, and URI contains a single user, as shown in the previous ...

