Take the following piece of code, which is vulnerable to buffer-overflow. Let's see how we can fuzz and exploit the vulnerability to get shell access to the system. We studied how to use Evans debugger in the earlier section. In this section, we will see how can we use gdb to exploit buffer overflows.
The following is given a simple code snippet written in C that asks the user for their name. Based upon the supplied value from the Terminal, it greets the user with the greeting message Hey <username>:
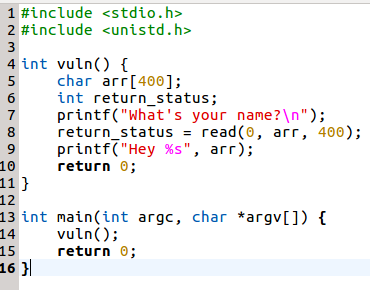
Let's compile the application by disabling the stack protection using the following command:
gcc -fno-stack-protector ...

