Chapter 1. Fundamental Concepts of Blockchain
It’s important to understand that blockchain is not a simple concept for most to grasp without a solid understanding of its origin, core components and architecture, as well as the debates surrounding blockchain. Blockchain has many slightly varying definitions that elicit some very dogmatic opinions, and this confuses many when first beginning their blockchain journey. This confusion happens because blockchain is not a tangible thing that can be touched or seen; instead, it is a concept born out of algorithms, technology, and fresh ideas for the exchange of economic value.
In this chapter, we’ll explore the fundamental concepts of blockchain by first starting with a brief history of its origin. This background information will help you understand why blockchain has no single standardized and universally accepted definition.
Following our discussion on blockchain’s origin, we will look briefly at several core components. Then we’ll delve into its architecture, followed by supporting technology and concepts.
In our look at the core components, we begin with the decentralized network. Then we cover cryptography. You can think of cryptography as the secret sauce of blockchain because it is what makes blockchain work. Without cryptography, there would be no use for blockchain. Next, we discuss ledger implementation. The ledger represents the storage or database in blockchain. It maintains the state created as a result of the last committed transaction as well as the history from the beginning of the ledger’s creation.
Next, we discuss the consensus, a protocol to find “agreement” among the nodes, which is the heart of blockchain. Consensus provides a secure means to complete transactions without relying on the traditional intermediaries in common transactional systems. Finally, we discuss smart contracts. The power in blockchain to perform complex transactions is a direct result of the employment of smart contracts. You can think of smart contracts as software programs.
This chapter will help you understand the following:
-
The architecture and core design components of blockchain
-
How ledger databases and world state databases work in blockchain
-
The role of cryptography (such as public/private keys or hash functions) in blockchain
-
The most popular consensus algorithms used in blockchain
-
How smart contracts work in a blockchain system
What Is Blockchain?
In the generally accepted definition, blockchain is a subset of distributed ledger technology (DLT). Breaking down DLT, we get distributed by creating a peer-to-peer network of nodes, which are computers; together they form a distributed network (Figure 1-1). Each node processes transactions submitted by clients. These transactions become committed records—called the ledger—of a replicated database on all nodes. This ledger is immutable, and the records are grouped into blocks.
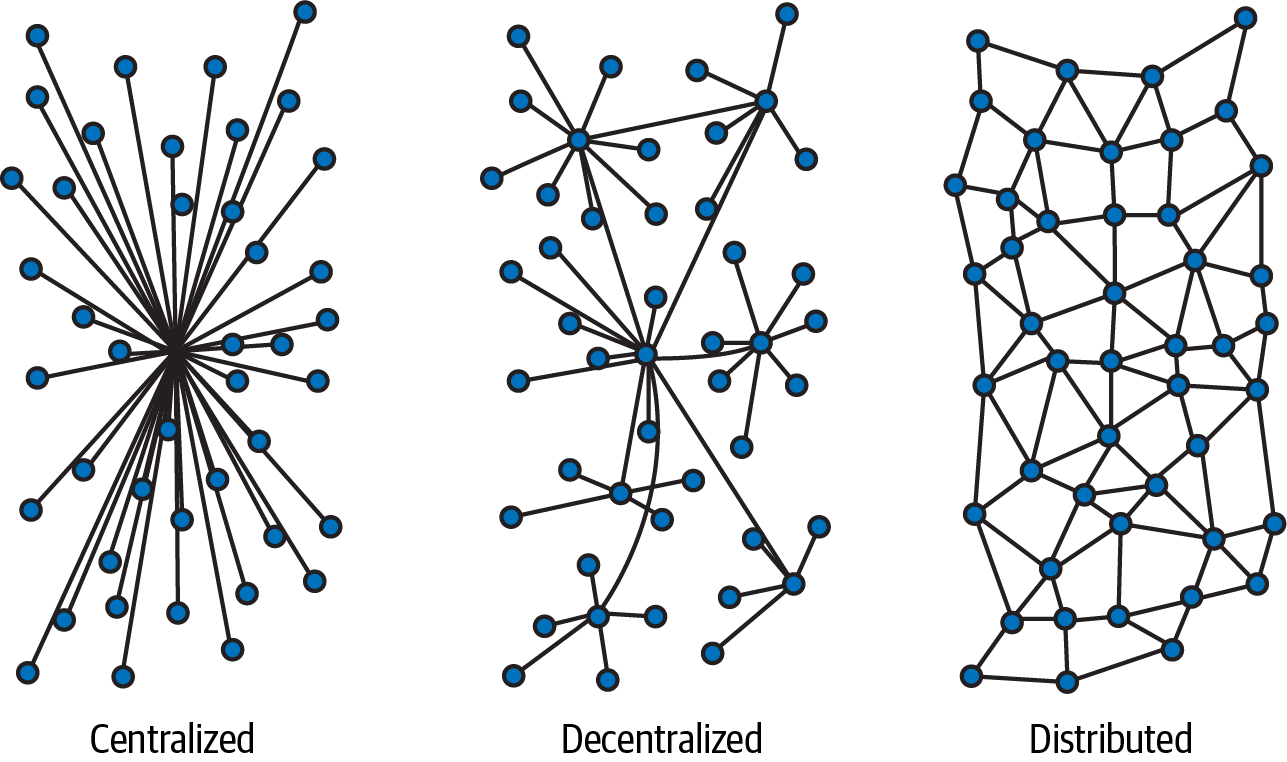
Figure 1-1. Types of networks
Each node maintains a copy of this immutable ledger, typically implemented as an append-only file or database. Blockchain relies on the employment of digital signatures and consensus to commit records. Most DLTs do not use consensus; instead, DLTs require only digital signatures to be present to commit records. There is no consensus, just digitally signed transactions.
The records are committed to the immutable ledger. In this append-only database, each record is ordered in time, and each block of records is cryptographically linked to the prior committed block. Each block contains additional metadata along with the hash code of the prior block and a set of committed records. The records are typically represented by a hash tree known as a Merkle tree (Figure 1-2).
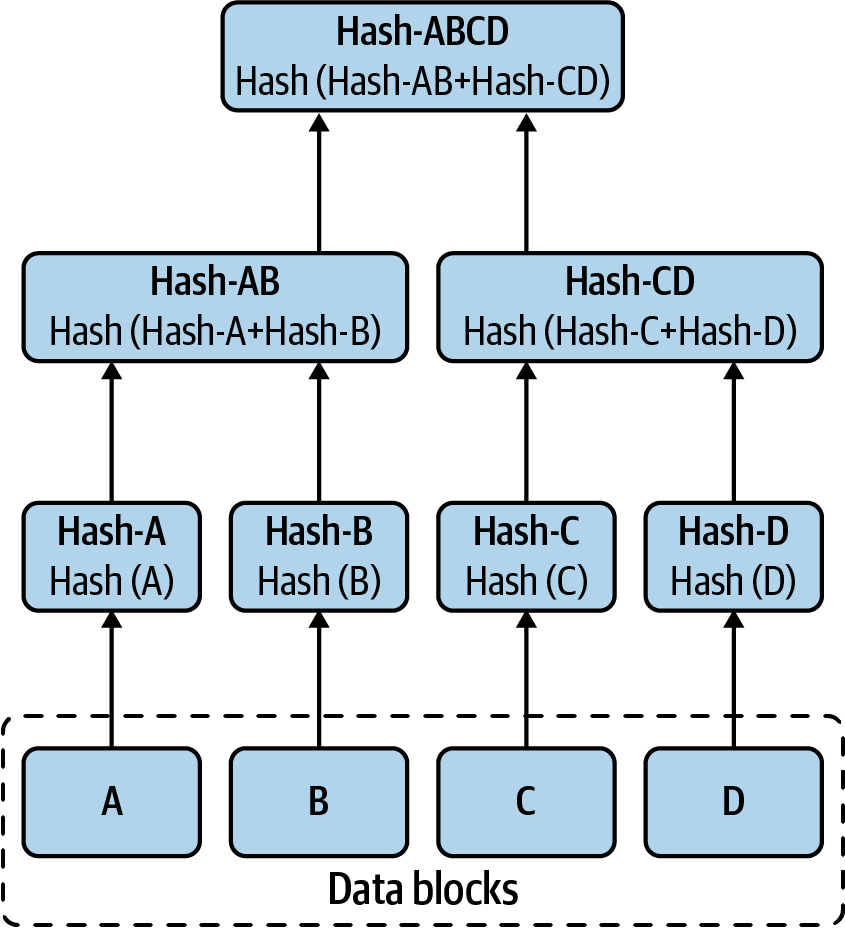
Figure 1-2. A Merkle tree
This gives you a general idea of what blockchain is. But we can begin to gain greater clarity when we look at its origin, its architecture, and its components. The origin explains why definitions diverged. Blockchain’s architecture is the easiest aspect to grasp because it is the most concrete of the topics and provides a holistic view. The components are a set of legacy technologies and logical concepts, each of which can be separately understood. By examining the components, we can build a solid foundation for mastering the skills required to develop blockchain smart contracts and blockchain applications. Understand that blockchain technology is built on legacy technology such as digital signatures, peer-to-peer networking, and decades of prior work.
Synergistic in nature, blockchain comes into existence when several legacy technologies join together as a single, complex, integrated system performing the fundamental task of executing transactions. Many, when discussing blockchain, see it as a database. Others see it as a transaction processor. Still others see it as a decentralized utopia free from any central control and a way to restructure society. Blockchain is all of these and more. Unfortunately, this paradigm is why it can be difficult to grasp the fundamental concept of blockchain.
Typically, new technologies or inventions are defined by a single purpose or well-understood solution to a problem. For instance, the concept of NoSQL databases is easy to understand. Even software-defined networking is not a stretch to envision and define.
Many try to understand blockchain by equating it with Bitcoin, the cryptocurrency that employs blockchain technology. This happens because blockchain technology is the underlying mechanism that facilitates the operation of Bitcoin, and thus they are seen as one. You should understand that Bitcoin is an application using blockchain technology. The Bitcoin use case is a peer-to-peer financial exchange. To understand blockchain, we will break it down into discrete components. Then you can combine them and envision solutions to problems you want to solve.
Origin of Blockchain
Most people date the birth of blockchain with the beginning of Bitcoin—more specifically, the Bitcoin paper authored by Satoshi Nakamoto and published in 2008. Who is Satoshi Nakamoto? Nobody knows, because they have never made themselves publicly known. They could be a person, group, company, or government agency, like the US National Security Agency (NSA). Regardless, Nakamoto remains a mystery.
There are those who claim to be Nakamoto, but no concrete proof has ever been presented. So, Nakamoto remains an unknown figure.
In Nakamoto’s paper, “Bitcoin: A Peer-to-Peer Electronic Cash System”, you will not find the term blockchain or block chain. The closest you’ll find is chain of blocks. You must go to code line 596 in main.h to find the first instance of the term block chain.
Satoshi cited eight papers, including “How to Time-Stamp a Digital Document” by Stuart Haber and W. Scott Stornetta, which contains the phrase chain of time-stamps. This, no doubt, was inspiration for how to link blocks of transactions together in the design of Bitcoin. Other cited papers must have influenced the design. First was “Protocols for Public Key Cryptosystems” by Ralph C. Merkle, who was famous for the Merkle tree (see Figure 1-2), a cryptographic hash tree data structure widely used in blockchain. The other paper of great influence was “b-money” by Wei Dai, which was certainly thought about while designing Bitcoin to be a digital cryptocurrency for use as a peer-to-peer exchange of value.
The Blockchain Revolution
Bitcoin was the spark that ignited the revolution of blockchain, but not the fuel for it. It also generated a subculture around Bitcoin with strong beliefs and a sense of ownership. This sparse and federated community, bound together by the common belief that “blockchain is only permissionless,” immediately took ownership of Bitcoin and replicated it into hundreds of incarnations. Some were identical and some divergent, but all united in a common thesis that represented an anarchist’s view of a new world possible with Bitcoin.
Blockchain 2.0
Prior to Bitcoin, Adam Back, known for Hashcash, wrote about a proof-of-work system used to prevent email spam in 2002. Nick Szabo developed the terms smart contracts in 1997 and bit gold in 2005, which many consider the precursors to Bitcoin. As far back as 1982, David Chaum, called the inventor of digital cash and inventor of blind signatures, was working on electronic cash. The concept of blockchain has a rich history and was fully developed in 2013 in “Ethereum Whitepaper” by Vitalik Buterin into what we think of today as Blockchain 2.0.
Prior to the Ethereum whitepaper, we had Blockchain 1.0, which powers Bitcoin and represents blockchain technology without the concept of the smart contract. In Blockchain 2.0, we have smart contract technology, which Buterin expressed in his whitepaper. It facilitates rich transactions far beyond the capability of Bitcoin, a platform for the simple exchange of value. With smart contract capability, intelligent stateful execution of complex transactions are possible. It is Blockchain 2.0 that started the blockchain revolution, the evolution of blockchain, and the attraction of enterprise organizations like IBM, Intel, Oracle, Amazon, Microsoft and many others, with the list expanding exponentially every day.
By 2015, after Ethereum became the first platform under Blockchain 2.0 to implement a single ledger, enterprise companies saw the potential of Blockchain 2.0. In December 2015, the Linux Foundation announced the creation of the Hyperledger project.
We cover the Hyperledger project in Part II, which contains two chapters. One covers the projects and tools, and the other covers the Hyperledger Fabric architecture and components. These two chapters provide the knowledge you will need for Part III, which covers smart contract development, invocation, maintenance, and testing. In the next section, we discuss, at a high level, the many components of blockchain.
Core Components of Blockchain
Blockchain is not a single compilation of source code. It may have a common executable, but both logical and physical components work together to form a functioning blockchain. This separation of logical and physical components may help create the confusion you see when discussing blockchain technology, along with the fact that blockchain is more of a concept than an implementation. Implementations of the concept are rapidly evolving and will continue to change and shift as more and more technologists and entrepreneurs enter the world of blockchain.
Common components form the central concept of blockchain. First is the decentralized network. Second is cryptography. Third is an immutable ledger. Fourth is consensus. And fifth is smart contracts. These five elements form the core components you need to create the concept of blockchain. The way they are implemented will evolve as new methods and algorithms are developed over time.
Which components you decide to use will shape your blockchain landscape and create a rich ecosystem of innovative solutions to new and existing problems. There are no rules.
Decentralized Network
A blockchain employs a decentralized network (depicted previously in Figure 1-1). Public blockchains allow anyone to participate, while private blockchains enforce membership, and only parties with a valid membership can participate in the blockchain.
Today there are two universally accepted types of blockchains: permissioned and permissionless. A permissioned blockchain requires a managing blockchain authority to enroll and grant membership to participate. The enrolled party may have rights to read only, or write only, or read and write. Hyperledger Fabric is a permissioned private blockchain.
A permissionless blockchain has no central authority, and anyone can participate. They can read and write the blockchain.
The network can be internal or external, or a combination. The network can be self-contained or span the world. Today we think of decentralized networks as made up of nodes when we consider blockchain. Any discussion, lecture, or presentation on blockchain will tell you that a blockchain must have a decentralized network of nodes. Depending on the speaker and target audience, the message will be biased to open, closed, or hybrid networks, but they’re always decentralized.
Cryptography
Cryptography is the blood of blockchain. It is the art of creating and keeping secrets. Since ancient times, people have needed to create secrets and send secret messages. Today complex mathematical algorithms are used to create secrets. To send the secret messages, protocols are used, which are rules for connecting and communicating the messages between parties. Without cryptography, there is no blockchain or DLT. The primary use of cryptography is for encryption, keys, hashing, signatures, integrity, proof, and tamper resistance.
Digital signatures
Digital signatures employ asymmetric cryptography, which employs a private and public key. Keys are pseudorandom generated bit strings. The private key is never revealed and kept secret. The public key, however, is revealed and distributed to the public or a designated party. Digital signing algorithms use the private key to encrypt text. The encrypted text can be decrypted by only the public key. Because the private and public keys are a pair, they work together and facilitate the creation of the concept of digital signatures.
Digital signatures have three primary uses. The first is for authentication. When someone signs a blockchain transaction with a private key, the receiver can authenticate the party that signed the transaction by using the party’s public key.
The second primary use is integrity. When a message is signed, any change in the message will invalidate the signature, and the receiving party will know the message has been tampered with.
The third important use is nonrepudiation. When a party signs a transaction and submits it, they cannot later try to claim they did not submit the transaction because their signature can be verified on the transaction submitted. They can claim only that their signature was stolen, but this too can be proven not true by employing additional signatures that belong to the device used to submit the transaction, including a timestamp and possible metadata that designates the location.
Hash functions
A hash function is a cryptographic one-way function. The function receives data as an argument, performs a cryptographic task, and then produces a string unique to the input data. If one bit of the input data is changed, the output string will change. If no bits are changed, the hash function will always produce the same output string.
Using a hash function in blockchain means you cannot change data, or the result will not match what is recorded. By linking the hash outputs into a Merkle tree, large numbers of records can be linked and stored in a block. The blocks are hashed, and the prior block’s hash is part of the next block, creating the immutable chain of blocks.
The Merkle tree is a hash tree structure in which nodes are hashed together successively until a single node is created. This single node provides the integrity for the entire tree. The bottom nodes can be rehashed and verified for data integrity.
Several secure hash algorithms exist, but SHA-256 and SHA-3 are the primary ones used in blockchain.
Wallet
Private and public keys are used a lot in blockchains. Private keys are used to sign transactions and represent the secrets you want to secure and protect. You place your keys in a digital wallet, just like you place your credit cards in your physical wallet. You may have a wallet for each blockchain, or you may have separate wallets for different applications. Wallets are containers for your keys. They secure them, manage them, and can facilitate the function of signing.
The functionality of wallets is growing, and they are becoming more sophisticated. There are physical wallets that plug into your USB and keep your keys safe in a hardware enclave, and software wallets that can exist on your computers or in the cloud. As time goes on, the function and features of wallets will continue to grow and expand.
Consensus
The concept of trust is the heart of blockchain. Consensus is the mechanism that facilitates the utopian aspect of blockchain by providing a means for disparate parties to transact without the necessary trust provided by intermediaries prevalent in today’s transactional systems.
Another way to think about consensus is this: every time you use your credit card, several intermediaries are involved, each performing a specific function and collecting a fee, which you are paying for in addition to the amount of your purchase. You may not see the fees, but they are built into the transaction either implicitly or explicitly, and you are paying for them. In blockchain, the mechanism of consensus performs this function of trust, void of intermediaries.
Consensus has many implementations. Each is designed to provide trust based on probability. This probability is a function of agreement. Complete agreement is difficult to attain and requires a lot of time and resources, while partial agreement is faster and requires fewer resources, but is risky. How much risk is tolerable depends on blockchain governance and determines the attributes of the consensus mechanism used to reach agreement. Seldom, if ever, can the probability of agreement be 1, or 100%, and often less than 100% is acceptable.
Many consensus algorithms exist, and new algorithms are continuously being designed. You should understand four: proof of work, proof of stake, practical Byzantine fault tolerance, and proof of elapsed time.
PoW
Proof of work (PoW) is a consensus algorithm used in Bitcoin and Ethereum (note that Ethereum is moving to proof of stake). This consensus algorithm relies on energy by solving a cryptographic puzzle. The energy is represented by the hashrate, which is the number of hashes generated per second. To generate a hash requires a finite amount of energy. This energy is the electricity used to produce a hash. The more hashes produced, the more energy required. The cost of energy is critical to the number of hashes that can be produced. The puzzle is to find an input that produces a hash number with a certain number of leading zeros. The complexity or average time to solve is controlled by designating the number of leading zeros.
For Bitcoin, the number of leading zeros is adjusted to keep the solving time around 10 minutes. Depending on how many miners are hashing, this number will vary up or down. This consensus model is energy dependent because miners who spend the most energy have a higher chance of finding the winning input and thus are rewarded with Bitcoin and get to commit the current block.
PoS
Proof of stake (PoS) is a consensus algorithm that depends on both randomization of and vested interest in the blockchain. Several PoS algorithms exist, but most employ routines for generating a random number from certain criteria such as the amount of coins held or the age of coins held. The lowest or highest random number generated wins and gets to commit the current block and receive a reward. Once a stakeholder wins, their stake criteria reverts to zero; this effectively eliminates them for the next round.
PBFT
Practical Byzantine fault tolerance (PBFT) is a consensus algorithm that dates back to 1999. PBFT is a leader-based nonforking algorithm. It requires all nodes to be connected to all other nodes. All the nodes are known, and the algorithm does not permit random nodes to join the peering group. The algorithm supports up to one-third of the nodes faulting. As long as no more than one-third of the nodes fault, consensus can be reached.
PoET
Proof of elapsed time (PoET) is a consensus algorithm that uses a trusted execution environment (TEE). In this algorithm, random peers are selected to execute requests at a predetermined rate. The selected peers sample an exponentially distributed random variable. They wait for time to pass, determined by the sample, and the peer with the smallest sample wins the election and gets to commit the block.
Smart Contracts
Blockchain applications are segmented into a client, smart contract, and blockchain. The client is the frontend that a user, either human or machine, interacts with to sign and submit transactions. The submission goes to a designated node, or peer, which accepts the transactions and forwards it to the smart contract. The smart contract executes the transaction in concert with the blockchain. This interaction between the smart contract and blockchain incorporates an API that the smart contract uses to perform specific functions exposed by the blockchain (for example, read or insert).
A smart contract can’t actually execute many functions against the blockchain because the blockchain is an immutable ledger. A smart contract can add or read data, but updating data is really an add data function that changes the current state. It cannot delete data even though it may execute an API for deleting data. The deletion is a change in state. This deletion would cause a read to return no data, but the data is there.
The data can be audited by using a special application called a blockchain explorer. This special program reads the immutable ledger at the lowest level, effectively crawling the data structure of the blocks and reading recorded data. A smart contract can do this too, but that would not be a typical use case.
A smart contract is best used to read the current state, perform logic on the state, and update (add) the state. Remember, the blockchain ledger is an immutable linked list of recorded data. That data represents the state. So the blockchain is really a running ledger of state transitions, a journal of immutable recordings. This is extremely powerful. Clients of the smart contract typically do the application-level logic and present the UX. Clients not only act as the interface to the smart contract, but in many ways, they represent the application to the user.
The thing to remember about the smart contract is it really isn’t that smart. It sits between the client and the blockchain. This is actually a good thing, because you don’t want the smart contract working that hard.
You don’t want to be making a lot of round trips between the client and ledger—for example, a thousand reads to populate a list. You want to tell the smart contract to read a thousand states and send them to your client. This executes a single call to the smart contract, an expensive resource, and the smart contract can potentially bulk-read on the ledger.
The typical interface is asynchronous, so keep this in mind and use your callbacks effectively. Try to give the user the perception of a lot of work being performed, when in reality, the blockchain is a turtle, not a rabbit like the databases we grew up with. Used wisely, smart contracts are powerful instruments; they can work for you or against you, so think about how you are using them. As a smart contract developer, you always want to keep your client in mind and support them with the most efficient API, based on what we have discussed.
Blockchain Architecture
The architecture of a blockchain consists of a decentralized and distributed network of nodes. Each node hosts a copy of the immutable ledger. The immutable ledger is a cryptographically linked set of append-only blocks. The nodes execute transactions and consensus to add blocks to the ledger. Clients sign transactions and submit them to the nodes. Nodes forward the validated transactions to the smart contracts for execution. Executed transactions are ordered and placed into blocks. The blocks are appended to the blockchain. The core design of a blockchain consists of blocks, chains, and a network.
Nodes
Computers are called nodes because of the role they play in creating the distributed network. They can be virtual machines in the cloud that are hosted by physical servers. They can be laptops participating in distributed networks. They can be Internet of Things devices operating in decentralized industrial networks. They can even be smart light bulbs. Node is a general term representing an endpoint in a network. The network can be wired or wireless. Another name for a node is peer, as in peer-to-peer networks, which are designed for decentralized applications.
For the Hyperledger Fabric blockchain, you will encounter both terms. In Hyperledger Fabric, the term peer represents a computing node that executes the endorsement and commitment of transactions and hosts an immutable ledger. In Bitcoin, nodes are miners, and like Hyperledger Fabric peers, commit transactions to the ledger.
Blocks
Blocks contain the records of submitted and committed transactions. Each block also contains a header, a timestamp, and the hash of the prior block. The first block, called the genesis block, contains additional information that describes the blockchain, like policies. If it’s in a permissioned blockchain, like Hyperledger Fabric, the genesis block will contain a list of member organizations and their certificates as well as policy information describing the number of organizations that must endorse transactions. It will also contain the identity of the orderer node responsible for ordering the transaction and creating the blocks that peers append to the blockchain.
The block contains additional data used to link the blocks together and provide integrity constraints, preventing any ability to tamper with the data contained in the block. The blocks are linked together, and this linking of blocks is responsible for the term blockchain.
Cryptography is used to create and maintain the blockchain data structure and linking. The block is tamper-proof because of the use of the cryptography.
The blocks together represent the immutable ledger, and many refer to them as the blockchain database. Blocks are appended to the last block created. Over time, this appending process creates a large data structure that must be managed. Other data structures are in use, like graphs, that are not linear and create network-like data structures. Data in a transaction is not always stored in the block and may be hosted in a traditional data store such as files or existing database technology.
Chains
Chains are a linked list of blocks. They are immutable and append-only. A blockchain architecture may have one or more chains. Chains can grow to an infinite length, or number of blocks. This can be prevented or managed by pruning, but pruning has side effects that reduce the trust in the blockchain network and remove the ability to explore and audit the entire chain. This can reduce the integrity of the chain.
Channels
Each blockchain in Hyperledger Fabric is called a channel, which is a consortium of organizations collaborating to execute transactions that are related to a specific purpose. Organizations in Hyperledger Fabric may belong to multiple channels. Bitcoin and Ethereum use a single main blockchain and multiple blockchains for test purposes.
Supporting Technology and Concepts
Beyond the components (decentralized network, cryptography, immutable ledger, consensus, and smart contracts), you need to understand, or at least be aware of, many concepts and supporting technologies in order to develop a solid foundation for understanding blockchain. Let’s introduce each of these concepts and supporting technologies so you can later further your investigation and advance your knowledge over the course of your blockchain journey.
DLT
Distributed ledger technology is the parent of blockchain. With DLT, you use only digital signatures and do not use consensus, because you want scale and high throughput. It is consensus that creates the high latency and limits on scale in blockchain. This is why you see DLTs like Corda so popular in the financial and insurance sectors. When you have semi-trust among participants, as in insurance and banking, you can enforce remediation by relying on digital signatures; you can use DLT. But when you need a trust mechanism to enforce integrity among participants, as in supply chains, you want blockchain because the consensus mechanism provides this level of assurance and trust.
Decentralization
Blockchain is a decentralized technology. The ledger is hosted by a network of peer-to-peer nodes that form the decentralized network. The removal of a central control point is what creates the concept of decentralization. It is the ability to delegate control to all nodes that collaborate, to execute the goal of the network, that delivers power to blockchain. This delegated control and collaboration provides the means for performing consensus without a central authority influencing the outcome.
Peer-to-Peer
Blockchain networks are peer-to-peer networks. The network is designed to be decentralized. No central control exists in a decentralized network, and each peer (or node) is connected to one or more peers (or nodes) in the network. The peers cooperate to send and forward messages in the network. Using peer-friendly protocols like Gossip enables the fast replication of messages among numerous peers in a network. This allows millions of peers to receive messages within seconds. A peer-to-peer decentralized network facilitates the ability to maintain copies of a blockchain ledger.
Immutability
The concept of immutability, which means not changeable, or tamper-proof, is critical to blockchain, because it is the primary attribute of the ledger. Trust is created from the concept and implementation of immutability. Knowing that time-ordered transactions are immutable allows parties to create trust and finality.
Identity
Blockchain and smart contracts need identities to function. Identities represent the entities (humans and machines) that participate in executing smart contract transactions and blockchain administration. For enterprise blockchains, organizations that are members enroll identities to represent them and perform transactions on behalf of the organization. Identities are assigned private and public keys for digital signing and encryption of data. The digital signatures authenticate the identities and authorize them to perform transactions.
Accounts
The concept of accounts in blockchain enables us to perform a variety of roles and to execute a multitude of functions for a single identity. An account is a record of attributes that define specific rights for access and authorization to perform transactions on assets that belong to or are managed by the account. Roles are created and assigned to an account. The role defines a set of permissions mapped to an account. Identities are granted a role, which allows the identity to perform actions against the account permitted by a role. This means we do not need to create and manage an identity for every account permissioned to execute transactions on a blockchain. Accounts allow us to partition the roles and permissions available to one or more identities. Accounts can hold various forms of state and transact as a trusted entity on the blockchain.
SDK
A software development kit (SDK) is used to integrate or develop software for a blockchain. Most developers are familiar with this component because many applications provide an SDK to develop software for their application. Blockchain is no different; most blockchain platforms provide one or more SDKs, each targeting a programming language and specific component of the platform. Several SDKs are available for Hyperledger Fabric, including JavaScript, Java, and Go, for developing Fabric blockchain applications.
API
An application programming interface (API) is a software contract between the application and client, expressed as a collection of methods or functions. The API may be implemented with an SDK or as a RESTful interface. It defines the available functions you can execute. Some APIs have hundreds of methods or functions you can call to execute a variety of transactions. Others may have fewer than a dozen and target a very narrow and specific set of application features.
The API is the intermediary interface between the client and the application. It must be managed well and support the continued evolution of the application’s life cycle. Versioning is often used to control and provide ease of migration to new or deprecated functionality.
Blockchain is an application and has an API. It is the API that smart contracts embed and expose to clients. The embedded API and exposed API are not the same intermediary. The exposed API is meant for the clients of the blockchain’s smart contract facility, while the embedded API is an internal contract between the smart contract facility and the core blockchain software responsible for operating the node, or peer. The smart contract facility may or may not be hosted by the node, or peer.
Transactions
Clients submit transactions. These transactions are processed by the nodes, or peers, and, if accepted, committed to a block that is appended to the chain of blocks (or blockchain). Transactions can be anything, from a data update about an asset to the payment for a service or the purchase of a product. They may be simply the recording of information representing a known state or the execution of an action. Transactions can originate from human clients or machine clients. Transactions in blockchain are always timestamped and ordered. They are immutable and cannot be tampered with. Transactions are signed with a private key when submitted for processing and may be authenticated depending on the blockchain permission for transaction submission.
Incentives
Incentives are rarely discussed in blockchain, and this hampers the success of many blockchain projects. A strong incentive is needed to create the behavior required to succeed in blockchain. The miners of Bitcoin know what incentive is because it is what drives them to mine. As a result, they execute transactions for clients and maintain the immutable and trusted blockchain that facilitates the exchange of value that clients seek to perform for a small fee. Their incentive is a reward if they can solve a cryptographic puzzle. The reward is a sizable monetary grant represented in Bitcoin.
For blockchains in the enterprise, there has been little or no incentive along the lines of Bitcoin or Ethereum. The absence of incentive has been a major reason for so many projects failing to succeed. Without a strong incentive, external partners have little reason to become enthusiastic about changing their mature business processes. They see only added cost and risk. The financial modeling, if done, is not enough to convince them this is a better and more efficient way to execute the business processes performed.
Privacy
Keeping data and the identity of the participants of a transaction private is a major concern in blockchain. The ability to disclose selectively and operate on data that cannot be exposed is critical to blockchain’s advancement. When several parties need to transact and exchange information, they should adhere to data privacy. Likewise, when specific parties want required data to execute their portion of a complex transaction, that data must be kept private.
One weakness in blockchain until recently has been the inability to mix varying levels of privacy within complex transactions. Hyperledger Fabric v2 supports the ability to perform transactions with private data. Within Hyperledger, work is being performed on zero-knowledge proofs (ZKPs). This cryptography facilitates the ability to prove facts without disclosing the source material used to determine a fact. Think of verifying an age without presenting the documentation that proves the age. This is powerful because it will allow transactions that protect the privacy of parties to the transaction. Because blockchain is a linked ledger and keys may represent parties or addresses, it is possible to build profiles that reveal enough information that could reduce the privacy a party thinks they possess. This is true with Bitcoin and Ethereum.
State
Blockchain has history, but it is the state we most often want. Being an immutable ledger of state transitions over time is what blockchain is built for. But when we put blockchain to use, we find it is the current state that manifests its power. We believe in the state because we know it was hard-earned, going through a gauntlet of validation and cryptographic proving. We enjoy the knowledge that it is tamper-proof, which adds even more value to the state.
But the state is not history. Blockchain has the history, but we find that accessing that history is expensive and not something the blockchain is really all that good at—that is, at scale. Because at scale, it is all about capturing state, reaching consensus, and committing it. We have learned to keep the state fresh and cached and to put the history in a traditional database. If we need to prove the history, we can walk the ledger and prove the history. But history is history. State is what matters. You make your decision based on state. State can be a rolling record—for example, sales to date. You don’t need to run those reports to get state.
This is a sea change and a huge boost in productivity. Blockchain will change the world because the world will know the current state, now, not tomorrow, or at the end of the week or quarter. The ability to maintain accurate and trustful state is a powerful tool to be leveraged and exploited by smart contract developers to empower decision makers, be they human or machine.
Turing Complete
The addition of the concept of Turing complete to blockchain was a turning point for blockchain’s separation from Bitcoin. It made blockchain a smart transactional engine for the 21st century. Smart contracts need to be Turing complete and deterministic to reach finality. Being deterministic allows them to be decentralized and scaled. Turing complete and deterministic capabilities enable consensus mechanisms to perform the function of intermediaries, delivering a means to reach agreement on state and finality.
Gas
Ethereum employs the concept of gas. This means you pay to compute, and the fees to compute are calculated by the instructions you execute. This concept is not new; mainframes charged users to compute, and calculated fees based on CPU time. In the world of the web, it is an explicit cost. We all pay fees to compute, but we cannot quantify them because of the layers of access and resources used. The closest we can get to the gas model is the Amazon Web Services (AWS) cloud computing service, which charges by the resource and time of use. AWS is much coarser than Ethereum’s granular cost model.
The volatility of Ether and all cryptocurrencies is problematic for trying to budget and launch applications on the Ethereum platform. With AWS, the currency is dollars, so you have a reasonable expectation of your long-term costs to launch and budget the resources required to operate your application. Your costs effectively do not vary from day to day, let alone minute to minute, as on Ethereum.
In addition to the gas cost, you are using a shared resource and are thus competing directly with others who want to execute their application and will pay more for the opportunity. This can lead to a situation where you may never get your transactions executed or not get them executed within the time period required to achieve your goal.
Tokens
Most will equate tokens with cryptocurrency, but they are evolving and will continue to evolve as they move further and further from the Bitcoin and Altcoin communities. A token is a digital voucher that can be exchanged. Tokens can be classified into types.
The first is cryptocurrency, the first blockchain token. Note that cryptographic tokens have been around a long time and have been used for various purposes like identity and metadata. The newest token, a derivative of cryptocurrency, is called a stable coin. It is called a stable coin because its token value is designed to equal the token value of another token, currency, or asset that does not exhibit large value fluctuations. The term pegged represents this value relationship between the stable coin and the other token, currency, or asset, which the stable token is designed to mirror in value. For example, stable coins pegged to the US dollar are valued at one dollar plus or minus a very small change in value on the order of hundredths or thousandths of a dollar at any point in time. Stable coins were promoted by Goldman Sachs and Circle to create stability in cryptocurrency and offer a means for established companies to explore cryptocurrency.
Crypto tokens, in the world of blockchain, are classified as cryptocurrency, security tokens, and utility tokens. You will find a variety of other names, but you need to focus on security and utility tokens.
Security tokens are sold to investors through various means, including initial coin offerings (ICOs) and security token offerings (STOs). Security tokens are considered securities, which are regulated by the US Securities and Exchange Commission (SEC). Therefore, you cannot sell (issue) them without registering with the SEC. They are treated no different from stock.
Utility tokens are like Ethereum’s gas. These are tokens you can sell, but have no air of investment surrounding them. The blockchain uses utility tokens as an internal means of operation. Creating and trying to sell utility tokens is risky. You should talk to legal professionals and seek a no-action letter from the SEC. You do this by submitting a detailed plan that explains how you will use the utility tokens. Some companies have received a no-action letter from the SEC and serve as a model for what the SEC considers utility tokens. Utility tokens do not appreciate and may fall in value, but no reward is associated with their purchase. They typically equal one dollar and can be redeemed for one dollar. An escrow account holds the funds exchanged for the utility token.
Tokens are an exciting opportunity for innovation in smart contract development and blockchain use. They can be smart, hold value, and represent assets and rights.
On-Chain
When we execute work on the blockchain, this is referred to as on-chain. Or, when we store data on the blockchain, it may be referred to as on-chain data. Be judicious when deciding what data you store on-chain because the blockchain as it exists today is not suitable as a data warehouse. You should store transaction data off-chain (explained next). When you want to rapidly execute large numbers of transactions, you should investigate executing the transactions off-chain.
Off-Chain
The ability to move work off the blockchain and perform it external to the blockchain is known as off-chain. Once the off-chain work is performed, the result is moved back on-chain to be committed via consensus to the blockchain. This is reasonable if you want to execute 10,000 rapid transactions, roll them up into one transaction, and then move that one transaction back on-chain to be subjected to consensus and committed to the blockchain. The off-chain transactions can be recorded on what is known as a side-chain and maybe via a DLT for fast execution. The Merkle tree of the transactions (shown previously in Figure 1-1) is placed into a single transaction and placed on-chain for consensus and commitment to the primary blockchain.
Scalability
Scalability is one of blockchain’s biggest problems. Blockchain employs consensus, and this creates latency in the processing of transactions. Reaching agreement, which is what consensus is all about, takes time. Time is what you need to eliminate if you want to scale. You cannot reach consensus en masse. A lot of research and design work is going into solving this problem.
The finance and insurance sectors have decided to use only DLT, which does not use consensus, as discussed earlier. They can do this because their sectors have an element of trust built in due to being highly regulated industries. For sectors like supply chain, trust needs to exist between parties. This trust has been accomplished by intermediaries. Employing intermediaries carries a significant cost, both in dollars and efficiency. The promise and attraction of blockchain is to eliminate or greatly reduce the need for intermediaries by employing consensus. Scalability is an area of concern that all blockchain projects must plan for in their application design.
Cryptocurrency
Bitcoin is a cryptocurrency, or digital asset, designed to be used as money. Hundreds of cryptocurrencies exist. You can think of cryptocurrency as digital cash. That was the inspiration behind its design, but that design has failed to manifest. Instead, it has become an asset like gold, with a devout following and marketplace for daily trading as the price fluctuates.
Few vendors accept cryptocurrency because of its volatility. Fiat money, the currency issued by central banks like the Federal Reserve, is stable for the most part. It, too, could experience a wide variance but is not volatile like cryptocurrency.
Most use cryptocurrency as a high-risk long-term investment, hoping it will appreciate, or as a trading vehicle trying to capitalize on the volatility. Central banks are now looking at moving into the issuance of cryptocurrency and adopting the term digital cash because it has many benefits for cross-border and trade finance payments.
Cryptocurrency is supported by blockchain technology and DLT. By using cryptocurrency and blockchain, central banks and governments will be able to extend and control the movement and use of cryptocurrency, which they cannot do with cash.
Enclaves
When you need to sign a transaction, you must use your private key. Anytime you access your private key, you are open to attack and events that may destroy, corrupt, or steal your private key. If something happens to your private key, anything that requires it for access is lost. There may be no way for you to recover your private key, and thus the asset or access granted is lost forever.
You store your keys and anything else digital in an enclave, which you use to perform the signing of transactions for you. Enclaves come in two forms: hardware and software. They are like private vaults that allow no entry without a secret password or elaborate ritual. Using an enclave prevents the key from being exposed, thus protecting and safeguarding it. Enclaves can perform their own transactions too, so they can be used to execute routines you want to keep secret.
J.P. Morgan’s Quorum blockchain, a modified clone of Ethereum, uses an enclave to perform its cryptographic functions, providing a level of security warranted by a regulated financial institution. The Hyperledger Sawtooth blockchain uses Intel’s Software Guard Extensions (SGX), which is a hardware enclave. Sawtooth uses the enclave for executing a secure version of its PoET consensus algorithm.
Oracles
When a blockchain needs external data or verification of internally submitted or generated data, it reaches out to an oracle. This is an API, interface, or website that can be scraped for information.
A smart contract that is a betting application, gold futures application, or loan application, for example, needs to know external information. The betting application needs to know who won the game last night, so it scrapes the USA Today Sports page or a paid site that offers sports scores for the outcome of the game. The gold futures application accesses the Wall Street Journal or a paid brokerage site for the current price of gold. The loan application accesses a site publishing current interest rates.
Oracles can also be other smart contracts. The idea behind the oracle is that it is an external source of valid, trusted information.
DApps
Decentralized applications, or DApps, are smart contract–based applications that seek to provide the same type of applications found on the web, from games to financial applications. DApps require fees to operate, unlike web applications. While many DApps exist, few have reached great success, except for a few used to trade virtual goods. The most popular are gambling DApps, which are not allowed in the United States. DApps suffer because of the UX and fees required to operate them.
DApps have not entered the enterprise space but may begin to emerge and transform as enterprises adopt blockchain and as a general-purpose hybrid blockchain is launched and goes viral. A hybrid blockchain spans the enterprise and public space and is architected along a federated design pattern. None exist today.
Virtual Machine
In blockchain, when we talk about a virtual machine (VM), we are talking about smart contract engines. The first blockchain virtual machine was the Ethereum Virtual Machine (EVM), which established Blockchain 2.0. Since then, it has been cloned, extended, and enhanced by other blockchains. The VM executes the smart contract.
Fork
When a blockchain splits for any reason, it creates a fork, which is a diverging chain of blocks, thus creating two versions of the blockchain. This can be seen as a negative or positive event. If all participants agree to the fork and it is managed, then it is positive. This can happen when an update is needed, a severe bug is found in the blockchain software, or a corrupting event has taken place and correction is needed.
Governance
How you manage and control a blockchain is determined by the governance model or function. Governance is important for the operation of the blockchain, and without it, a blockchain will not last long. It needs governance to manage the life cycle, which includes upgrades, failures, participant rules, and operational constraints.
Clients
Transactions are submitted to the blockchain by clients. Clients will sign their transaction by using their private key (or keys) and send the signed transactions to a blockchain node. Nodes then replicate the received transactions by sending them to known nodes; eventually, all the nodes have a copy of the client transactions. Clients may host wallets to store their keys and maintain receipts of committed transactions securely.
Summary
This chapter covered a lot of information to help you begin to understand the concept of blockchain. We began with a discussion on the origin of blockchain. Then we discussed several general components of blockchain, followed by its architecture, shared ledger, cryptography, consensus, and smart contract components. We kept the discussion at a high level so you could assimilate the fundamental concepts and formulate your own interpretation based on the knowledge we provided. We hope you research each item in greater detail as your blockchain journey continues and you master smart contract development.
In Part II, we’ll discuss the Hyperledger project and tools, followed by the Hyperledger Fabric architecture and components, to provide you with the necessary knowledge for Part III, where we cover smart contract development with Hyperledger Fabric.
Get Hands-On Smart Contract Development with Hyperledger Fabric V2 now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

