Chapter 11. Network Security: Get Defensive

The network’s a dangerous place to make a living.
Attackers lurk around every corner: rootkits, and script kiddies, and bots... oh my! You’ve got to buck up and harden your network, or the barbarians will crash the gates. In this chapter, we expose you to the seedy underworld of the network, where attackers spoof MAC addresses, poison your ARP cache, infiltrate your internets, sneak packets into your network, and trick your co-workers into coughing up their passwords. Get defensive, dude! Let’s keep our precious data in and the interlopers out.
The bad guys are everywhere
You’ve put together crucial services like DNS, you’ve used troubleshooting to keep your network free of bugs, and you’ve set up a wireless network. The last thing you need now is someone infiltrating your network and messing up all the crucial data you have flying back and forth at top speeds.
As a network professional, you need to protect your networks from the bad guys and stop them from stealing information and launching deadly attacks on your servers.
It is not unusual to have a new server attacked within minutes of being turned on.
The evil impersonator
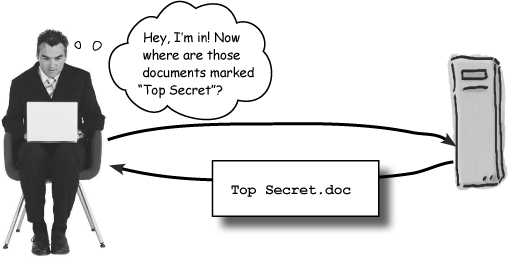
The evil attacker
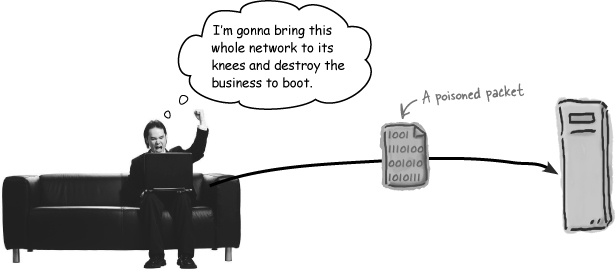
And it’s ...
Get Head First Networking now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

