A slightly closer look at how the Container does Authentication and Authorization
On the last page we skimmed over what the Container was doing. Throughout this chapter we’ll hit different levels of detail, and here we zoom in just a little...
The Container perspective...
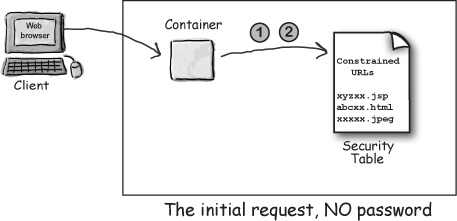
1 Having received the request, the container finds the URL in the “security table” (stored in whatever the Container is using to keep security info).
2 If the Container finds the URL in the security table, it checks to see whether the requested resource is constrained. If it is, it returns 401...
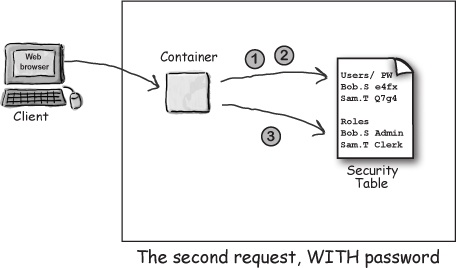
1 When the Container receives a request with a username and password, it checks the URL in the security table.
2 If it finds the URL in the security table (and sees that it’s constrained), it checks the username and password information to make sure they match.
3 If the username and password are OK, the Container checks to see if the user has been assigned the correct ‘role’ to access this resource (i.e. authorization). If so, the resource is returned to the client.
Get Head First Servlets and JSP, 2nd Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

