March 2008
Intermediate to advanced
911 pages
20h 31m
English
Content preview from Head First Servlets and JSP, 2nd Edition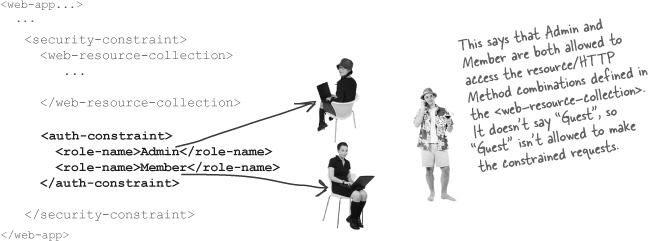
Become an O’Reilly member and get unlimited access to this title plus top books and audiobooks from O’Reilly and nearly 200 top publishers, thousands of courses curated by job role, 150+ live events each month,
Start your free trial



Picky <security-constraint> rules for <auth-constraint> sub-elements
Even though it’s got constraint in its name, this is the sub-element that specifies which roles are ALLOWED to access the web resources specified by the <web-resource-collection> sub-element(s).
The <auth-constraint> sub-element of <security-constraint>
