802.1x Authentication Conversation
Here's how authentication works (Figure 6.3):
Figure 6.3. 802.1x protocol.
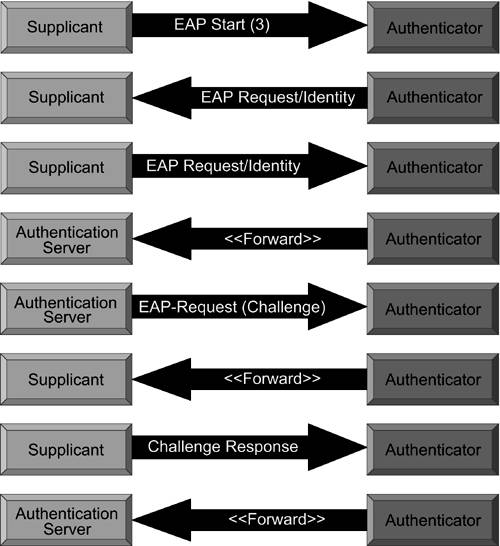
The supplicant (client) starts by sending an EAP Start frame. This lets the authenticator know that somebody's knocking and wants in. The authenticator replies with an EAP Request/Identity frame, which is like saying, “Who's there?” The supplicant replies with another EAP Request/Identity frame identifying themselves (i.e., a username). The authenticator forwards this information to the authentication server.
The authentication server then sends the authenticator an EAP-Request frame which contains some kind of challenge or request for ...
Get How Secure Is Your Wireless Network? Safeguarding Your Wi-Fi LAN now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

