Exploitation
Abstract
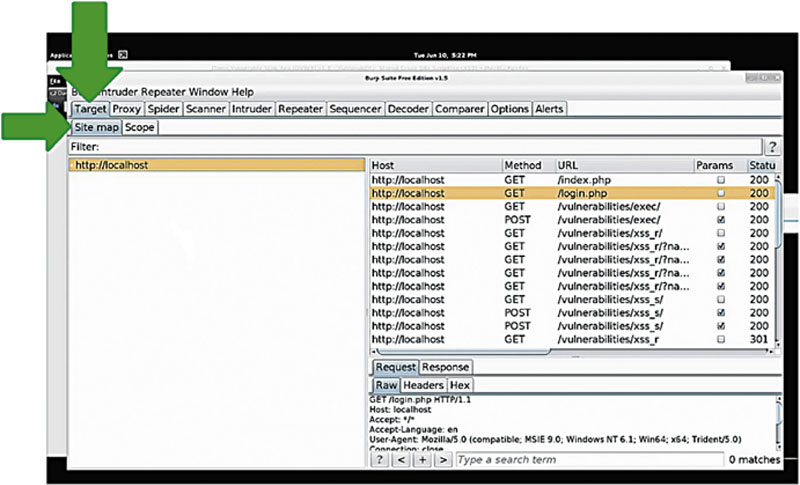
We take a closer look at the Burp Suite site map and Spider. This chapter then covers bypassing client-side controls, cross-site scripting (XSS), and how to use Stored XSS to deface a website.
Keywords
Get How to Attack and Defend Your Website now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

