Applying Cryptography to HTTP
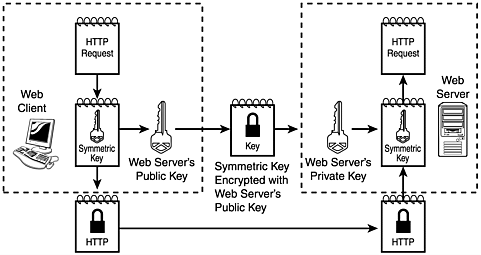
SSL is basically a protocol that employs both symmetric and asymmetric cryptography to protect messages that use TCP as the transport-level protocol. Because of the high performance expense of asymmetric cryptography, it is only used to exchange the randomly generated symmetric key that is then used for the symmetric encryption of the HTTP messages. Figure 18.5 illustrates this point. The same symmetric key is used as long as the TCP connection remains open.
Figure 18.5. SSL utilizes both symmetric and asymmetric cryptography.
When used to protect Web communication, SSL’s position in the protocol stack is just ...
Get HTTP Developer’s Handbook now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

