4.7. Approaches for securing e-business solutions
This section summarizes the security solutions using the architectures described in 4.5, “Techniques for securing the end-to-end model” on page 120.
4.7.1. Securing e-business using packet filtering and application firewalls
In the scenario illustrated in Figure 4-24, there is a business requirement to provide external access to enterprise data and applications.
Figure 4-24. Hosting solution using packet filtering and application proxies
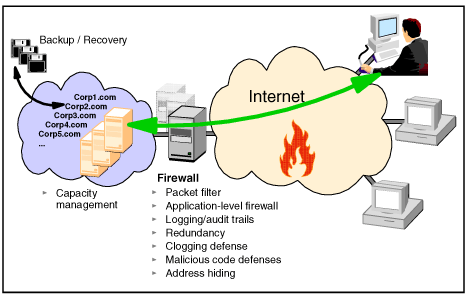
In this scenario, the security and management requirements include:
Address hiding to provide a level of confidentiality
Protecting the integrity of the enterprise ...
Get IBM e-business Technology, Solution, and Design Overview now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

