9.2. Microsoft 802.1x
When it comes to 802.1x, many people immediately think of Wireless LAN security. In reality, 802.1x is port-based authentication that can apply to both wired and wireless networks. With authentication being a requirement for port access, this technology can be used to keep unwanted users off of the LAN. In doing so, this is performing an NAC/NAP function.
802.1x consists of two primary components:
Supplicant — Requests access to a network.
Authenticator — Authenticates supplicants and decides whether or not to grant them access. This can be a wireless access point (WAP) or a Remote Authentication Dial-in User Service (RADIUS) Server
To completely understand 802.1x, you must understand controlled and uncontrolled ports. A controlled port controls to what network addresses communication can take place. Uncontrolled ports allow unrestricted access. Figure 9-1 illustrates controlled and uncontrolled ports.
Figure 9-1. Controlled and uncontrolled ports
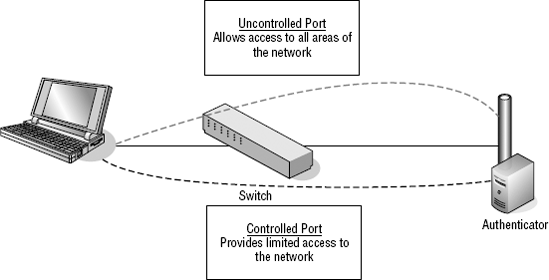
By having all devices that are connecting to the LAN placed onto a controlled port, their access is limited to just the Authenticator. This protects the network from having just anyone plug in and gain access. Once authenticated by the Authenticator, the device is placed onto an uncontrolled port and access to the network is unrestricted.
Clearly, the 802.1x functionality can prohibit just any device from gaining ...
Get Implementing NAP and NAC Security Technologies: The Complete Guide to Network Access Control now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

